PluXml CMS is a widely used content management system (CMS) for personal and small website environments. The recently discovered CVE-2025-57567 vulnerability resides in the theme editor feature within the service's admin panel, allowing an authenticated administrator to inject arbitrary PHP code, potentially leading to remote code execution (RCE).
This vulnerability is extremely dangerous, as a successful attack can result in complete server control. Given the active exploitation of similar attacks, it is possible that this vulnerability was used in an actual attack. Therefore, all customers using PluXml CMS should immediately update to the latest version to protect against potential data leaks and system takeover attacks.
Our TA team is monitoring vulnerabilities in PluXml CMS and other web application services, and we will respond promptly to any additional product vulnerabilities discovered.
Tags: PluXml CMS, CMS, PluXml, CVE-2025-57567, RCE
Source: https://commons.wikimedia.org/
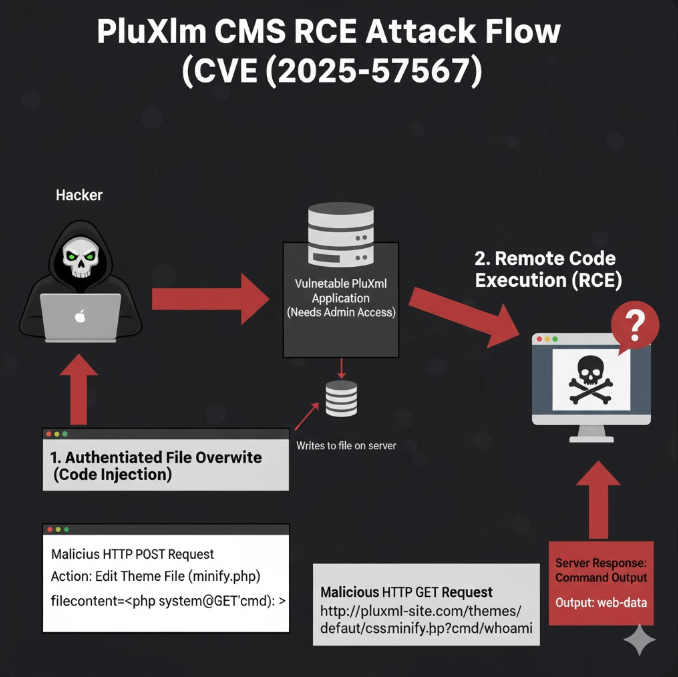
Malicious File Creation via Code Injection: PluXml’s theme editor allows administrators to edit and save theme-related files (such as CSS or template files). Attackers can exploit this feature to overwrite legitimate files with malicious PHP code—for example, injecting it into /themes/defaut/css/minify.php to create a web shell. Attackers send a request through the admin panel’s Theme Editor to overwrite the minify.php file. (The actual request includes session cookies and a CSRF token, encoded as form data.)
ex)
Remote Code Execution (RCE): Once the file overwrite is successful, the attacker can directly access the injected PHP file via a browser to execute arbitrary commands on the server. The modified minify.php file now functions as a web shell that runs PHP code and returns the output.
Example:
Immediate actions:
1. Apply the patch immediately: Update PluXml CMS to the latest version.
2. Temporary mitigations: If an immediate update is not possible, implement temporary security measures to minimize risk.
Our AIWAF product detects and mitigates this vulnerability through pattern 1404: Webshell.
CVE-2025-57567 occurs in the admin panel’s theme editor and allows authenticated administrators to perform RCE by injecting PHP code.
Since successful exploitation grants full server control and similar attacks are actively exploited, all users must update immediately.
The TA team continuously monitors vulnerabilities in PluXml CMS and other web applications and will respond promptly to new findings.
https://nvd.nist.gov/vuln/detail/CVE-2025-57567
This vulnerability is extremely dangerous, as a successful attack can result in complete server control. Given the active exploitation of similar attacks, it is possible that this vulnerability was used in an actual attack. Therefore, all customers using PluXml CMS should immediately update to the latest version to protect against potential data leaks and system takeover attacks.
Our TA team is monitoring vulnerabilities in PluXml CMS and other web application services, and we will respond promptly to any additional product vulnerabilities discovered.
Tags: PluXml CMS, CMS, PluXml, CVE-2025-57567, RCE
1. Overview
PluXml CMS is a free, open-source website management system based on PHP and XML architecture. This report analyzes the Authenticated Admin Remote Code Execution (CVE-2025-57567) vulnerability that occurs in the Theme Editor feature, allowing an administrator to manipulate server files and execute arbitrary code.
Source: https://commons.wikimedia.org/
2. Attack Type
This vulnerability arises when the application processes file modification requests from an authenticated administrator without verifying the safety of the content, allowing executable files on the server to be overwritten.
Malicious File Creation via Code Injection: PluXml’s theme editor allows administrators to edit and save theme-related files (such as CSS or template files). Attackers can exploit this feature to overwrite legitimate files with malicious PHP code—for example, injecting it into /themes/defaut/css/minify.php to create a web shell. Attackers send a request through the admin panel’s Theme Editor to overwrite the minify.php file. (The actual request includes session cookies and a CSRF token, encoded as form data.)
ex)
POST /core/admin/parametres_edittpl.php HTTP/1.1
Host: your-pluxml-site.com
Cookie: plx_session=...; plx_auth=...
Content-Type: application/x-www-form-urlencoded
Connection: close
Remote Code Execution (RCE): Once the file overwrite is successful, the attacker can directly access the injected PHP file via a browser to execute arbitrary commands on the server. The modified minify.php file now functions as a web shell that runs PHP code and returns the output.
Example:
GET /themes/defaut/css/minify.php?cmd=ls%20-la HTTP/1.1
Host: your-pluxml-site.com
User-Agent: Mozilla/5.0
Connection: close
3. Response
The CVE-2025-57567 vulnerability allows an authenticated administrator to inject PHP code via the Theme Editor, achieving remote code execution. Because this can grant full control of the server, the severity is considered critical.Immediate actions:
1. Apply the patch immediately: Update PluXml CMS to the latest version.
2. Temporary mitigations: If an immediate update is not possible, implement temporary security measures to minimize risk.
Our AIWAF product detects and mitigates this vulnerability through pattern 1404: Webshell.
4. Conclusion
PluXml CMS is a widely used CMS for small-scale websites.CVE-2025-57567 occurs in the admin panel’s theme editor and allows authenticated administrators to perform RCE by injecting PHP code.
Since successful exploitation grants full server control and similar attacks are actively exploited, all users must update immediately.
The TA team continuously monitors vulnerabilities in PluXml CMS and other web applications and will respond promptly to new findings.
5. References
https://github.com/lukehebe/Vulnerability-Disclosures/blob/main/CVE-2025-57567.pdfhttps://nvd.nist.gov/vuln/detail/CVE-2025-57567


