AIONCLOUD's
Zero Trust Network Access(ZTNA)
AIONCLOUD ZTNA secures access to internal private applications for remote users
without exposing them to the cyber threats.
What is Zero Trust Network Access(ZTNA)
Zero Trust security is a major focus and buzzword in the digital business era. As changes in the work
environment reveal limitations of traditional security products, there's a growing interest in adopting
security based on the Zero Trust paradigm. Zero Trust Network Access(ZTNA) stands out as a central
security solution among Zero Trust-based security solutions.
ZTNA is a security solution that provides secure and seamless Zero Trust access to a company's private applications for remote users from anywhere at any time. It is fundamentally based on the concept of Zero Trust, which means it trusts nothing whether inside or outside the security perimeters.
ZTNA operates based on a Software-Defined Perimeter (SDP) approach rather than network- centric security, which assumes that no user or device should be trusted by default, regardless of whether they are inside or outside the network. Access to applications is strictly controlled and granted on a need-to-know basis. ZTNA strictly verifies context-based information such as user identity and device identity before granting "Least-privileged access," ensuring data security and integrity.
ZTNA plays a central role in the Secure Access Service Edge (SASE) framework or Security Service Edge(SSE) as one of its most critical components, working in conjunction with security services like SWG, CASB, and FWaaS to ensure secure access control.
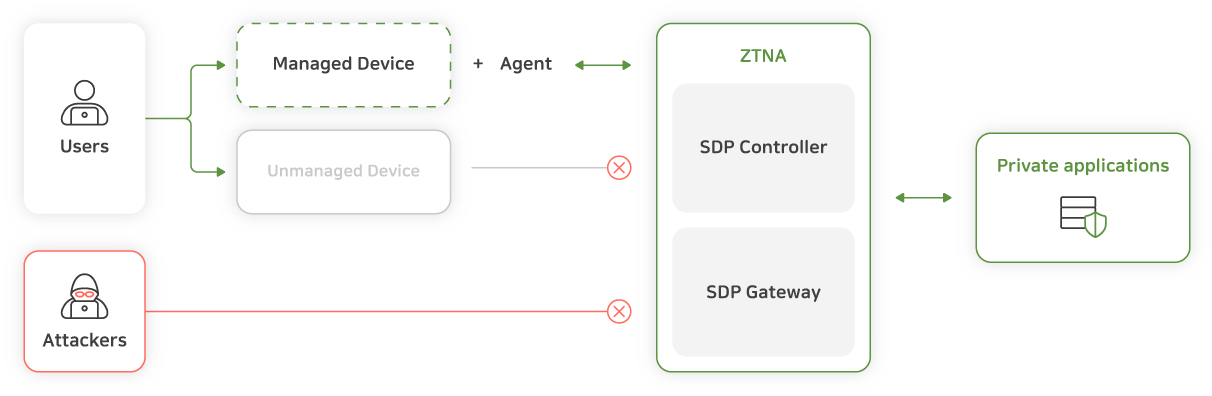
ZTNA is a security solution that provides secure and seamless Zero Trust access to a company's private applications for remote users from anywhere at any time. It is fundamentally based on the concept of Zero Trust, which means it trusts nothing whether inside or outside the security perimeters.
ZTNA operates based on a Software-Defined Perimeter (SDP) approach rather than network- centric security, which assumes that no user or device should be trusted by default, regardless of whether they are inside or outside the network. Access to applications is strictly controlled and granted on a need-to-know basis. ZTNA strictly verifies context-based information such as user identity and device identity before granting "Least-privileged access," ensuring data security and integrity.
ZTNA plays a central role in the Secure Access Service Edge (SASE) framework or Security Service Edge(SSE) as one of its most critical components, working in conjunction with security services like SWG, CASB, and FWaaS to ensure secure access control.

Benefits of ZTNA
The adoption of the ZTNA model has brought numerous advantages
and benefits to enterprises. Here are some of the various benefits that ZTNA provides:
ZTNA completely replaces traditional access control security
products like VPN.
VPNs are vulnerable to threats such as Man-in-the-Middle attacks
and lateral movement attacks, and they demand substantial bandwidth costs
to support access for all remote users.
ZTNA dramatically simplifies the delivery of security to the business
with direct and secure connections to private applications,
significantly reducing network complexity and costs,
thereby alleviating the burden on enterprises to maintain security.
VPNs are vulnerable to threats such as Man-in-the-Middle attacks
and lateral movement attacks, and they demand substantial bandwidth costs
to support access for all remote users.
ZTNA dramatically simplifies the delivery of security to the business
with direct and secure connections to private applications,
significantly reducing network complexity and costs,
thereby alleviating the burden on enterprises to maintain security.
ZTNA supports secure remote access to private
applications.
With the legacy soluition, users had to connect to the corporate network
to access applications. However, ZTNA allows access to applications
without the need for a connection to the corporate network,
using a Zero Trust-based security tunnel for access.
It completely conceals the infrastructure within the public network,
providing a secure remote access environment and significantly
reducing the risk posed by network threats.
With the legacy soluition, users had to connect to the corporate network
to access applications. However, ZTNA allows access to applications
without the need for a connection to the corporate network,
using a Zero Trust-based security tunnel for access.
It completely conceals the infrastructure within the public network,
providing a secure remote access environment and significantly
reducing the risk posed by network threats.
ZTNA enables granular access control
for users accessing applications.
Traditional perimeter-based security approaches allow access
to the entire network for any users with valid login key.
ZTNA, through strict user authentication based on device posture checks
and a 'need to know' approach, grants least-privileged access.
It supports application- specific access policies,
eliminating the need for complex network segmentation.
Traditional perimeter-based security approaches allow access
to the entire network for any users with valid login key.
ZTNA, through strict user authentication based on device posture checks
and a 'need to know' approach, grants least-privileged access.
It supports application- specific access policies,
eliminating the need for complex network segmentation.
The difference between VPN and ZTNA
Many businesses have traditionally relied on VPNs as a means for
secure access management to their corporate network and resources for end users. However, with the rise
of hybrid work environments, the number of long-term remote workers has increased, revealing limitations
of VPN such as lack of scalability and high maintenance costs. Additionally, the growing adoption of
public cloud services has made it challenging to apply consistent security policies to remote workers
located outside the network security perimeter.
The demand for an alternative to ineffective traditional services has surged dramatically, and ZTNA is the exact solution for this demand.
The demand for an alternative to ineffective traditional services has surged dramatically, and ZTNA is the exact solution for this demand.
| VPN | ZTNA | |
|---|---|---|
| Access control | VPN grants access to the entire network to all users with valid login credentials. An attacker possessing the login key can gain network access, attempt lateral movement attacks, and potentially steal critical business-facing asset. | ZTNA provides the least-privileged access to organization segmented applications only for authorized users. It applies different access policies to users and organizations according to the company's compliance requirements, effectively preventing threats such as lateral movement and data leakage. |
| Device posture | VPN does not conduct independent checks on the devices during the process of connecting the user to the corporate network. Network access from devices infected with malware, viruses, or those in need of critical vulnerability updates can pose significant threats to the corporate network. | ZTNA verifies the posture of all devices attempting to access corporate applications. Based on the device security posture, ZTNA applies adaptive access, and if any threats are detected on the device, it terminates the connection immediately to minimize security risks. |
| Security monitoring | VPN does not provide visibility into the user's action, once user entered a company's network. In particular, there is a lack of visibility into the application layer, such as web and cloud SaaS usage, making it vulnerable from a security standpoint. | ZTNA logs the activities of all users and enforces data-centric control through deeper visibility and real-time monitoring. Additionally, it can be integrated with third-party solutions like SIEM and EDR to enhance security even further. |
| User Experience | The additional encryption and routing processes of VPNs can result in temporary internet performance degradation. Moreover, the physical distance from the user's connection point to the VPN server and the presence of multiple intermediary nodes in the network backbone can hinder user experience. | ZTNA ensures that all use traffic is directly connected to the desired segmented application without routing through data centers or backhauls, guaranteeing high- speed connections. |
check compare table
AIONCLOUD ZTNA
Secure Remote Access
AIONCLOUD's Secure Remote Access (SRA) is a ZTNA solution
that enables granular Zero Trust access to private applications from any location and device. As a
unified cloud-native security service, SRA, in conjunction with the SSE platform Secure Internet
Access (SIA), can be easily deployed and seamlessly replaces legacy network solution.
SRA is a single-point security solution that enables
granular access management
for all users, all endpoints, and all applications.
for all users, all endpoints, and all applications.
Service can be initiated with fast and easy
deployment,
requiring no complex network configuration.
requiring no complex network configuration.
SRA supports Multi-factor Authentication (MFA) and Single
Sign-On (SSO). It enhances
remote access security by integrating with identity providers like AzureAD and OKTA.
remote access security by integrating with identity providers like AzureAD and OKTA.
All user traffic is routed through AIONCLOUD's global
edge
to the company's data centers or the cloud.
AIONCLOUD's edge network completely eliminates security challenges
of legacy VPNs, including unexpected network failures and latency issues.
to the company's data centers or the cloud.
AIONCLOUD's edge network completely eliminates security challenges
of legacy VPNs, including unexpected network failures and latency issues.
Cloud-scale remote access that eliminates the capacity
constraints
that have plagued the legacy appliance security model.
The cloud platform's flexibility and scalability allow users
to be added as needed without requiring special configuration changes.
that have plagued the legacy appliance security model.
The cloud platform's flexibility and scalability allow users
to be added as needed without requiring special configuration changes.

