We analyze a technique that abuses the dump functionality of Windows Error Reporting (WerFaultSecure) to temporarily freeze EDR/antivirus processes and manipulate their execution state.
An attacker supplies the target process's PID to WerFaultSecure, and during the collection of a dump for the protected process (PPL, Protected Process Light), WerFaultSecure suspends the target process.
The research PoC monitors when the target process becomes suspended and then manipulates WerFaultSecure's execution (e.g., by suspending or forcibly terminating it) to delay or control the moment when the target process resumes.
tags: EDR-Freeze, Vaccine, EDR, Suspend, Malware, Exploit, PoC
An attacker passes the target process’s PID as an argument to WerFaultSecure. During the process of collecting a dump of a protected process (PPL, Protected Process Light), WerFaultSecure suspends the target process.
The research PoC then monitors when the target becomes suspended, and manipulates WerFaultSecure’s execution (e.g., suspend or force‐terminate) to delay or control the exact timing of the target process’s resume.
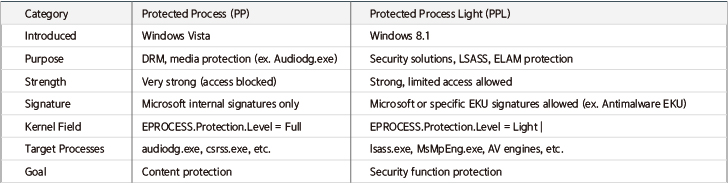
In conclusion, PPL is an OS-level protection mechanism designed by Microsoft to protect specific security processes (e.g., antivirus, LSASS) based on code integrity and signature trust.

The above image shows a PPL-protected process (Microsoft Defender), where Protected: “PsProtectedSignerAntimalware-Light” is the kernel display value.
Broken down by fields:
WerFaultSecure does not operate under normal user rights (including admin); details are covered further below.
The CreateProcessAsPPL function extends the CreateProcessW API using the extended structure (STARTUPINFOEX) and the PROC_THREAD_ATTRIBUTE_PROTECTION_LEVEL attribute:
Running a process with the regular CreateProcess API will not apply PPL. However, providing the STARTUPINFOEX structure and the PROTECTION_LEVEL attribute through CreateProcessW allows the request to reach the kernel.
If code integrity checks succeed, WerFaultSecure launches with PPL.
PPL (Protected Process Light) is an OS-level trust tier assigned only to binaries trusted by Microsoft's code-signing and integrity enforcement. Attackers exploit this trust to perform privileged OS-allowed actions (e.g., dumping protected processes, accessing restricted handles), thereby disabling or bypassing security solutions.
When launched, it runs as either a PP or PPL. The exact internal conditions determining PP vs PPL execution are not publicly documented.
When executed with specific arguments, WerFaultSecure invokes the MiniDumpWriteDump API to collect a process dump. During this operation, the target process is placed into a suspended state.
Below is evidence from Procmon and IDA Pro showing how the target is suspended and which functions are called:

The stack trace shows that WerFaultSecure imports dbgcore.dll, which contains:
In the dbgcore.dll module, it is possible to confirm that the MiniDumpReadDumpStream and MiniDumpWriteDump APIs are being used. Additionally, after examining the dbgcore.dll module through IDA Pro, we were able to find the following API functions that suggest the target process can be suspended

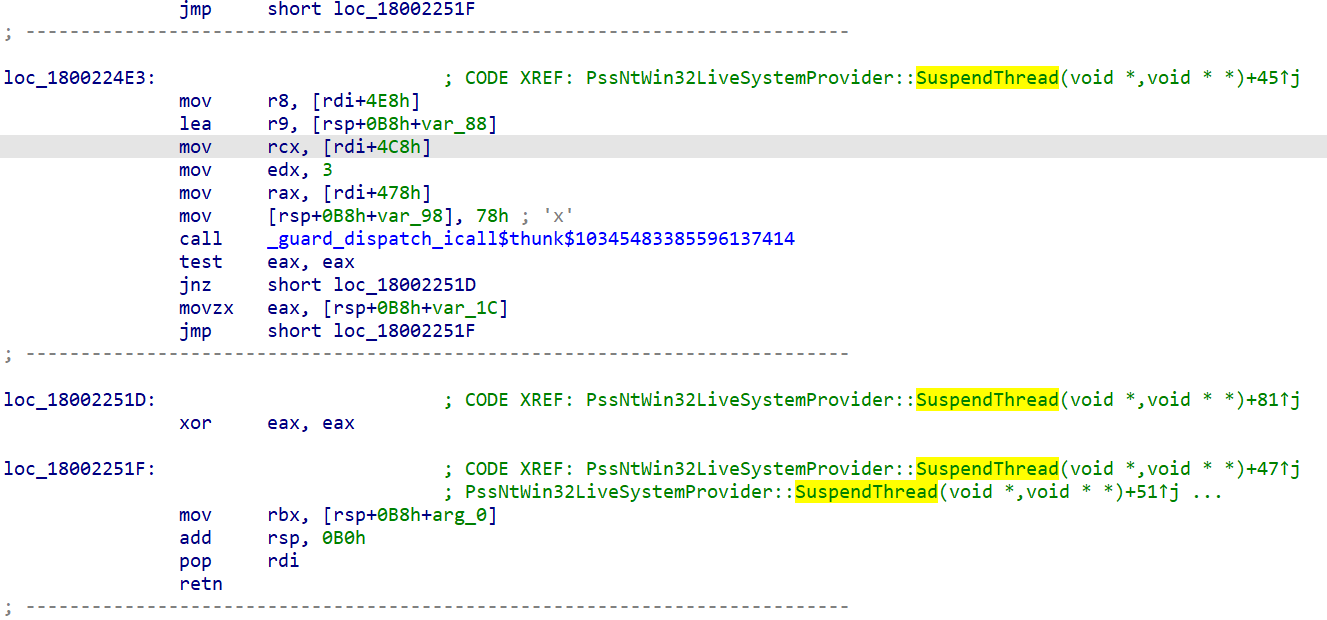
PssNtWin32LiveSystemProvider::SuspendThread
Pss* refers to Process Snapshotting Services, although official documentation does not cover the internals.
This strongly suggests that the target’s threads are suspended to ensure consistency during a live dump operation.
Antivirus and EDR vendors apply Microsoft's Protected Process Light (PPL) model by assigning the PsProtectedSignerAntimalware-Light protection level to their executables.
This prevents normal privilege levels from suspending those processes.
However, the EDR-Freeze technique abuses this very structure.
The attacker passes the target PID to WerFaultSecure, triggering a legitimate suspension, and then artificially maintains the suspended state—effectively freezing the EDR/AV process.
In other words: WerFaultSecure is the entity that suspends the process; the attacker merely exploits this behavior.
This behavior depends heavily on OS build, configuration, and execution context; therefore, it cannot be guaranteed to work uniformly across all systems.
Microsoft Defender detects this behavior as “Tampering:Win32/SuspWerFaultSec.A” (from Oct 1, 2025). Keeping endpoint security tools fully updated is essential.
https://www.zerosalarium.com/2025/09/EDR-Freeze-Puts-EDRs-Antivirus-Into-Coma.html
https://www.sysnet.pe.kr/2/0/13169
The research PoC monitors when the target process becomes suspended and then manipulates WerFaultSecure's execution (e.g., by suspending or forcibly terminating it) to delay or control the moment when the target process resumes.
tags: EDR-Freeze, Vaccine, EDR, Suspend, Malware, Exploit, PoC
1. Overview
We examine a technique in which the dump function of Windows Error Reporting (WerFaultSecure) is abused to temporarily freeze EDR/antivirus processes and control that suspended state.An attacker passes the target process’s PID as an argument to WerFaultSecure. During the process of collecting a dump of a protected process (PPL, Protected Process Light), WerFaultSecure suspends the target process.
The research PoC then monitors when the target becomes suspended, and manipulates WerFaultSecure’s execution (e.g., suspend or force‐terminate) to delay or control the exact timing of the target process’s resume.
2. What are PP (Protected Process) / PPL (Protected Process Light)?
They are Windows signature-based protection mechanisms. Protected Process / Protected Process Light were introduced starting with Windows Vista and Windows 8.1 respectively, and although they share the same concept, the application scope, signature policies, and intended purpose differ.
In conclusion, PPL is an OS-level protection mechanism designed by Microsoft to protect specific security processes (e.g., antivirus, LSASS) based on code integrity and signature trust.

The above image shows a PPL-protected process (Microsoft Defender), where Protected: “PsProtectedSignerAntimalware-Light” is the kernel display value.
Broken down by fields:
PsProtectedSignerAntimalware - Light
└──────────────┬──────────────┘ └──────┬──────┘
│ │
Signer = Antimalware Type = Light

3. WerFaultSecure Process Creation
The researcher who released EDR-Freeze uses the CreateProcessAsPPL function to launch the WerFaultSecure process.WerFaultSecure does not operate under normal user rights (including admin); details are covered further below.
The CreateProcessAsPPL function extends the CreateProcessW API using the extended structure (STARTUPINFOEX) and the PROC_THREAD_ATTRIBUTE_PROTECTION_LEVEL attribute:
// Create process with PPL protection
if (!CreateProcessW(
nullptr, // Application name
(LPWSTR)commandLine.c_str(), // Command line
nullptr, // Process security attributes
nullptr, // Thread security attributes
TRUE, // Inherit handles
EXTENDED_STARTUPINFO_PRESENT | CREATE_PROTECTED_PROCESS,
nullptr, // Environment
nullptr, // Current directory
&siex.StartupInfo, // Startup info
&pi)) // Process information
{
std::wcerr << L"CreateProcessW failed: " << GetLastError() << std::endl;
DeleteProcThreadAttributeList(ptal);
HeapFree(GetProcessHeap(), 0, ptal);
return 0;
}
Running a process with the regular CreateProcess API will not apply PPL. However, providing the STARTUPINFOEX structure and the PROTECTION_LEVEL attribute through CreateProcessW allows the request to reach the kernel.
If code integrity checks succeed, WerFaultSecure launches with PPL.
PPL (Protected Process Light) is an OS-level trust tier assigned only to binaries trusted by Microsoft's code-signing and integrity enforcement. Attackers exploit this trust to perform privileged OS-allowed actions (e.g., dumping protected processes, accessing restricted handles), thereby disabling or bypassing security solutions.
4. WerFaultSecure Process Behavior and Freeze Mechanism
WerFaultSecure.exe is part of Windows Error Reporting (WER), a legitimate Microsoft utility. Similar to WerFault.exe, it is a hardened version designed to handle crashes in protected processes.When launched, it runs as either a PP or PPL. The exact internal conditions determining PP vs PPL execution are not publicly documented.
std::wstring werPath = L"C:\\Windows\\System32\\WerFaultSecure.exe";
std::wstringstream cmd;
cmd << werPath
<< L" /h"
<< L" /pid " << targetPID
<< L" /tid " << targetTID
<< L" /encfile " << HandleToDecimal(hEncDump)
<< L" /cancel " << HandleToDecimal(hCancel)
<< L" /type 268310"; // dump full
std::wstring commandLine = cmd.str();
PPLProcessCreator creator;
//0 = WinTCB
DWORD werPID = creator.CreatePPLProcess(0, commandLine);
if (werPID == 0)
{
std::wcerr << L"Failed to create PPL process." << std::endl;
CloseHandle(hEncDump);
CloseHandle(hCancel);
return 0;
}
When executed with specific arguments, WerFaultSecure invokes the MiniDumpWriteDump API to collect a process dump. During this operation, the target process is placed into a suspended state.
Below is evidence from Procmon and IDA Pro showing how the target is suspended and which functions are called:

The stack trace shows that WerFaultSecure imports dbgcore.dll, which contains:
In the dbgcore.dll module, it is possible to confirm that the MiniDumpReadDumpStream and MiniDumpWriteDump APIs are being used. Additionally, after examining the dbgcore.dll module through IDA Pro, we were able to find the following API functions that suggest the target process can be suspended


PssNtWin32LiveSystemProvider::SuspendThread
Pss* refers to Process Snapshotting Services, although official documentation does not cover the internals.
This strongly suggests that the target’s threads are suspended to ensure consistency during a live dump operation.
5. Mitigation
EDR-Freeze PoC was released on September 21, 2025. Microsoft Defender added detection “Tampering:Win32/SuspWerFaultSec.A” on October 1, 2025. It is recommended to keep antivirus and EDR solutions updated so that this detection is applied.6. Conclusion
WerFaultSecure is a system utility related to Windows Error Reporting (WER). When a protected process (PP) fails, WerFaultSecure collects debugging information or memory dumps. During this process, the target is temporarily placed in a suspended state.Antivirus and EDR vendors apply Microsoft's Protected Process Light (PPL) model by assigning the PsProtectedSignerAntimalware-Light protection level to their executables.
This prevents normal privilege levels from suspending those processes.
However, the EDR-Freeze technique abuses this very structure.
The attacker passes the target PID to WerFaultSecure, triggering a legitimate suspension, and then artificially maintains the suspended state—effectively freezing the EDR/AV process.
In other words: WerFaultSecure is the entity that suspends the process; the attacker merely exploits this behavior.
This behavior depends heavily on OS build, configuration, and execution context; therefore, it cannot be guaranteed to work uniformly across all systems.
Microsoft Defender detects this behavior as “Tampering:Win32/SuspWerFaultSec.A” (from Oct 1, 2025). Keeping endpoint security tools fully updated is essential.
7. References
https://github.com/TwoSevenOneT/EDR-Freeze/tree/masterhttps://www.zerosalarium.com/2025/09/EDR-Freeze-Puts-EDRs-Antivirus-Into-Coma.html
https://www.sysnet.pe.kr/2/0/13169


