Weekly web attack trends
You can analyze weekly web attack trends to see when web attacks are concentrated at any given time. Based on this, you can use it to plan proactive prevention and response strategies for high attack periods.
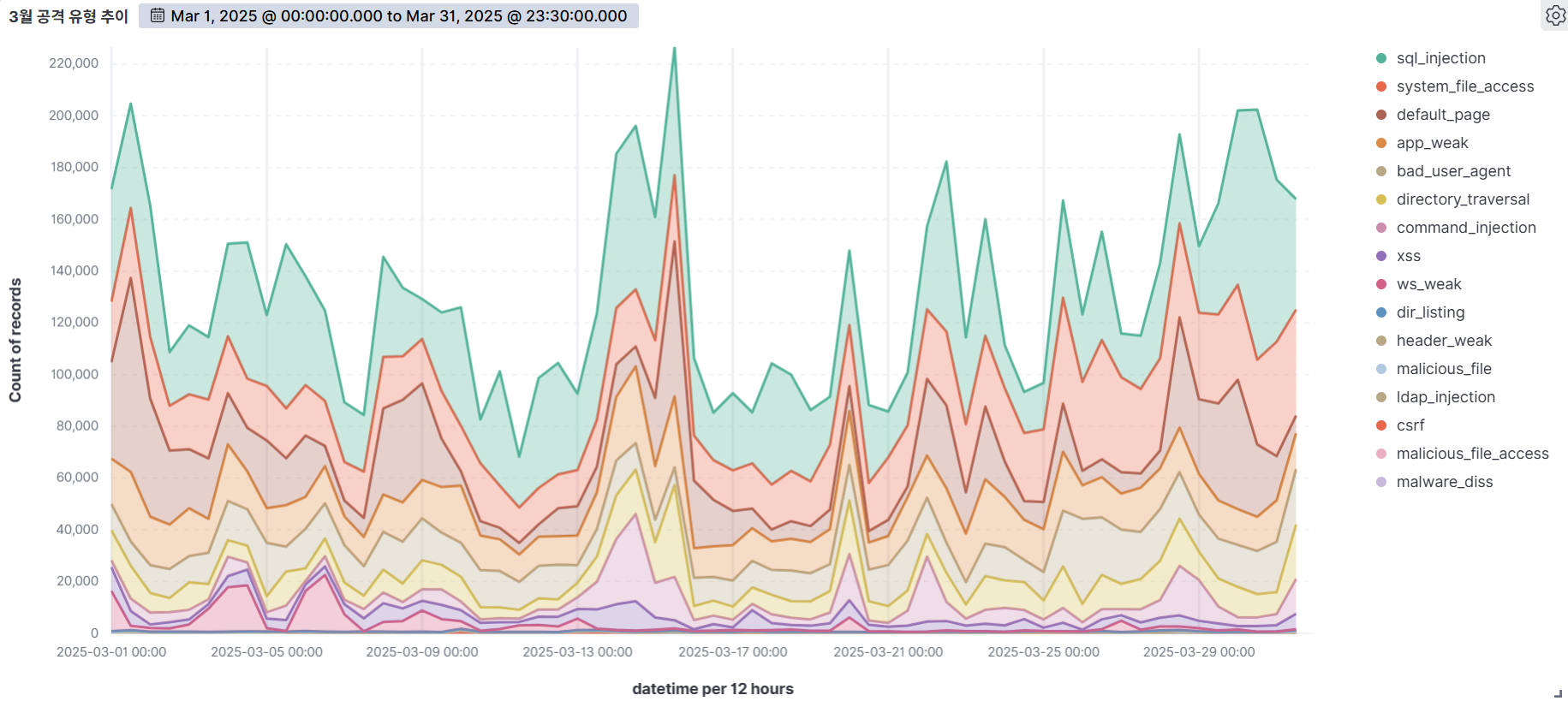
The graph below visualizes the number of web attacks detected by AIWAF during the month of April 2025, on a weekly basis.
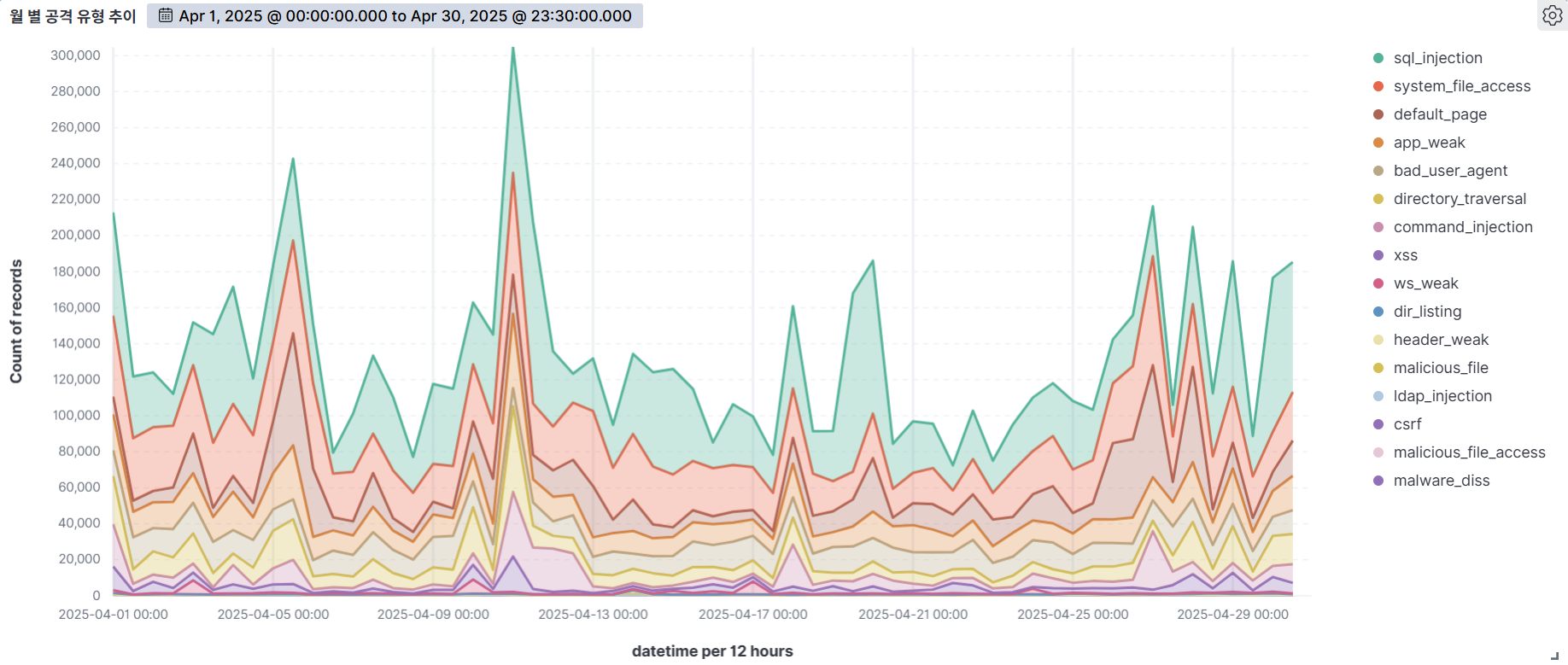
Analyzing AIWAF detected data for the month of April 2025, we detected an average of nearly 260,000 web attacks per day, an increase from the previous month, indicating that threats to web servers are continuing to become more sophisticated. We also observed a higher frequency of attacks on weekends (Saturdays and Sundays) than on weekdays, which could indicate a strategic approach to take advantage of lower web server utilization during non-business hours.
Notably, April 11 was the most intensive day for web attacks during the entire period, with SQL Injection accounting for the highest percentage of attack types detected on that day. SQL Injection is a common attack method that manipulates databases to take over system privileges or steal internal information. Attackers often use this technique to bypass a system's user authentication process or to gain insight into the database structure, which makes it especially important for organizations to protect their sensitive information. In fact, AIWAF categorizes SQL Injection as a high-risk attack type with the most detection patterns. The results of this analysis demonstrate that major web attack types, including SQL Injection, require continued attention and sophisticated response strategies, and will provide important evidence for future detection and blocking policies.
Web attack trends by attack type
By analyzing web attack trends by attack type based on detection logs, you can systematically identify which types of attacks are most frequent over the course of a month. This analysis is more than just a statistic; it is a key reference point for refining your organization's security policy and response.
Analyzing the detection logs collected by AIWAF during the month of April 2025, we detected a wide range of web attacks, some of which showed distinct patterns, such as being concentrated in certain time periods or accounting for a high proportion of the total number of attacks. In particular, classic and still threatening attack types such as SQL Injection and System File Access are at the top of the list, and they tend to be carried out repeatedly, often by automated attack tools or botnets.
The graph below visualizes the distribution of web attack types detected by AIWAF as of April 2025.
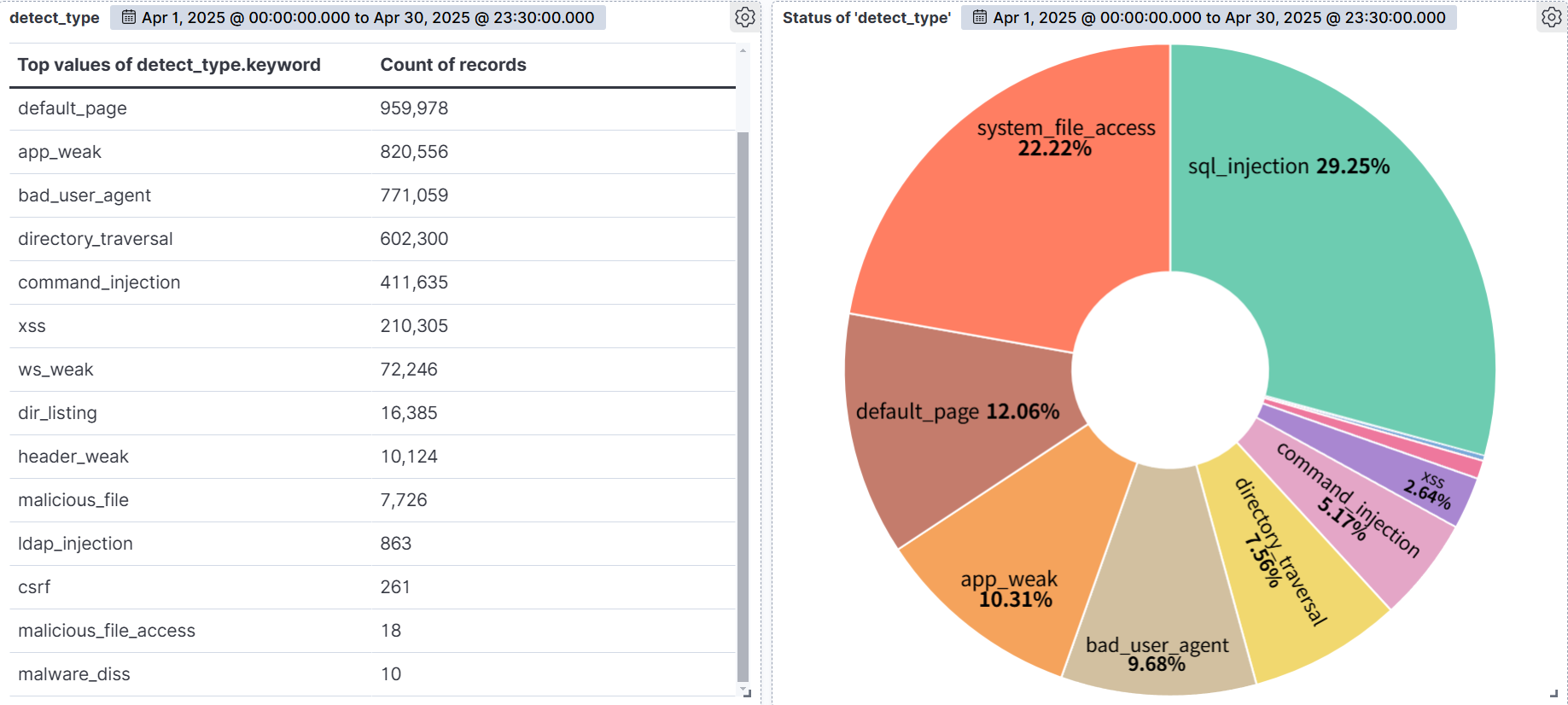
According to statistics by type of web attack detected by AIWAF in the month of April 2025, SQL Injection was the most prevalent, accounting for 29.25% of all detections. It was followed by System File Access (22.22%), Default Page (12.06%), and App Weak (10.31%). This suggests the need for more precise responses and proactive measures against this particular type of attack.
First of all, SQL Injection is a type of attack that is always at the top of the OWASP Top 10, and the attack techniques are highly evolving. This attack typically occurs when values passed via user input are included in the SQL query and executed verbatim, which can be exploited by an attacker to bypass unusual authentication, view database structures, steal sensitive data, and more. In particular, dynamic queries and lack of validation of input values make them highly vulnerable.
System File Access (22.22%), the second highest percentage, refers to attempts by attackers to exploit vulnerabilities in web applications to gain unauthorized access to files and directories inside the system or to manipulate arbitrary files. These attacks can be caused by web server configuration issues, insufficient access controls, directory path validation failures, etc. and can lead to system privilege takeover or backdoor installation if successful.
The third highest category, Default Page (12.06%), targets pages that retain their initial settings after installation or system message pages. They expose information during the information gathering phase that can be used in subsequent attacks to determine the type of software and configuration of the system. While this attack type is largely passive, it is often detected in high volume by automated scanners, making early detection and response critical.
App Weakness (10.31%), the fourth most common attack type, targets security flaws in the application itself, such as lack of authentication, session management vulnerabilities, and misconfigurations. It has been increasingly detected in cloud-based SaaS systems and API-based services in the form of authentication bypass attempts and API abuse, which may have implications for future cloud security policy formulation.
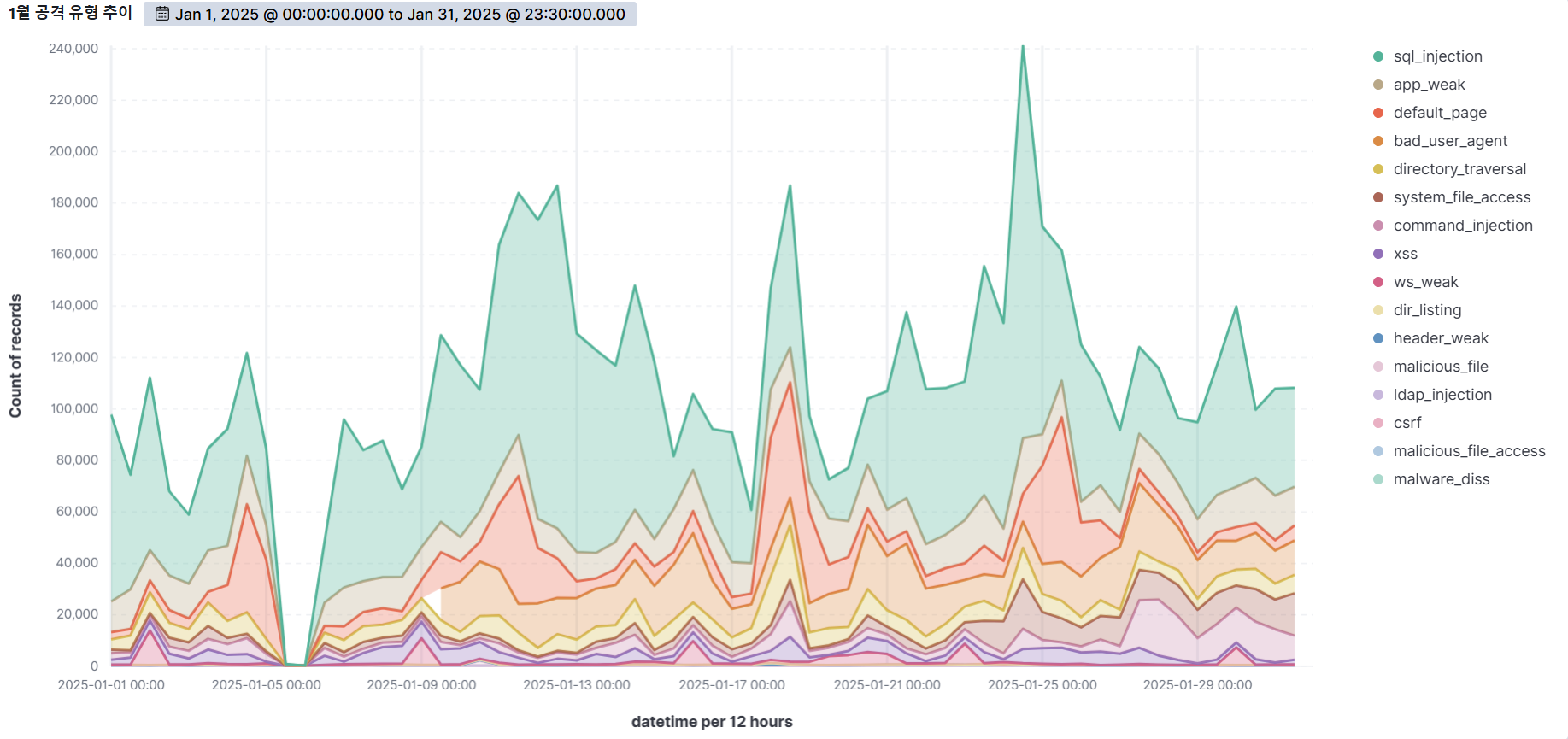
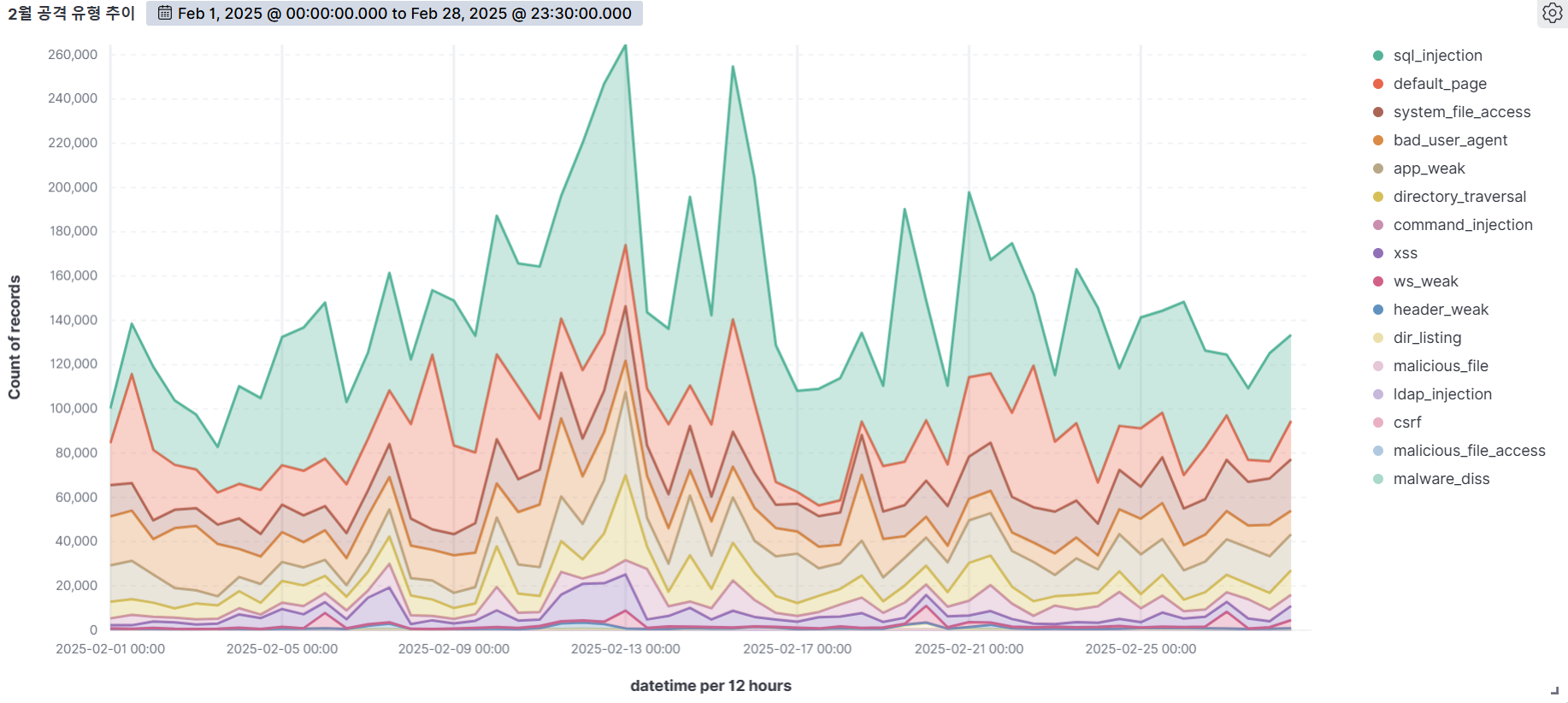
Summary of web attack trend graphs for the last 3 months
January
February
March
Top 30 Attacker IPs

Vulnerability analysis reports
HUNK COMPANION Plugin Remote Code Execution
1. Overview
The Hunk Companion plugin for WordPress is a plugin that contains the features you need to create a website, and we've analyzed it for CVE-2024-9707, an RCE vulnerability found in the plugin.

Source : https://www.bleepingcomputer.com/news/security/hunk-companion-wordpress-plugin-exploited-to-install-vulnerable-plugins/
2. Attack types
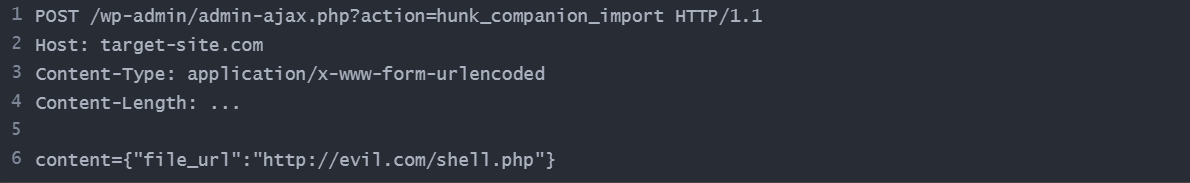
CVE-2024-9707 is a vulnerability in the Hunk Companion plugin for WordPress in all versions, including 1.8.4, due to missing functionality checks for the /wp-json/hc/v1/themehunk-import REST API endpoint, which allows unauthorized plugin installation/activation. This could allow an unauthenticated attacker to install and activate arbitrary plugins, which could be leveraged to achieve remote code execution once other vulnerable plugins are installed and activated.
Attack method:
- The attacker sends a crafted HTTP request to the /wp-json/hc/v1/themehunk-import endpoint.
- The request is processed without validating user authentication or permissions due to missing functional checks.
- The plugin specified in the request is installed and activated on the target WordPress instance.
Example attack syntax:
3. What to do
CVE-2024-9707 was addressed in a patch for the Hunk Companion Plugin in 1.8.5 or later.
The vulnerability appears to be attacked via a crafted HTTP request to the /wp-json/hc/v1/themehunk-import endpoint. We will be analyzing this further in our AIWAF product and responding to it as a pattern.
4. Conclusion
This critical vulnerability in the Hunk Companion plugin could be the first step in a broader exploitation chain. If other plugins with known vulnerabilities are enabled through this flaw, an attacker could achieve remote code execution on a WordPress site. The widespread distribution of WordPress, the popularity of ThemeHunk themes, and the critical nature of the flaw combine to make this a serious security risk.
In conclusion, this vulnerability highlights the importance of conducting proper security reviews and implementing strong authentication and authorization checks within software components. The broad impact and ease of exploitation make this a serious threat that requires immediate attention and remediation.
Our AIWAF product is responding to vulnerabilities in various plugins by developing patterns, and we will continue to respond to related vulnerabilities as they are discovered in the future.
5. References
- https://nvd.nist.gov/vuln/detail/CVE-2024-9707
- https://www.securin.io/vulnerability-notice/cve-2024-9707/
- https://www.incibe.es/en/incibe-cert/early-warning/vulnerabilities/cve-2024-9707
- https://wordpress.org/plugins/hunk-companion/
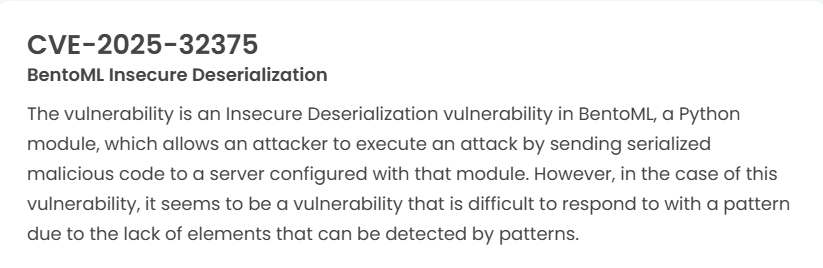
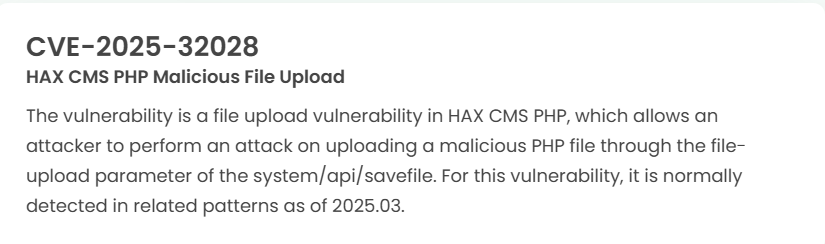
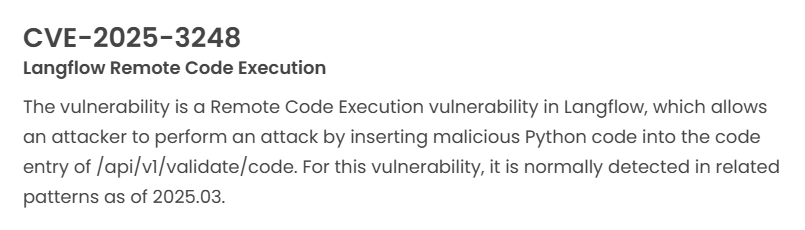
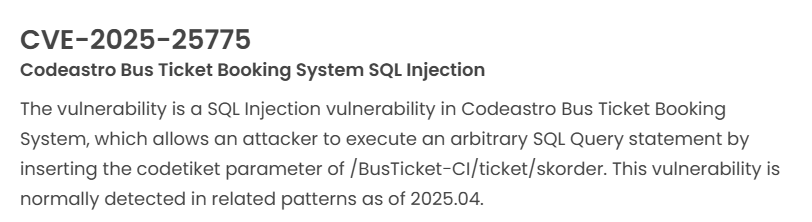
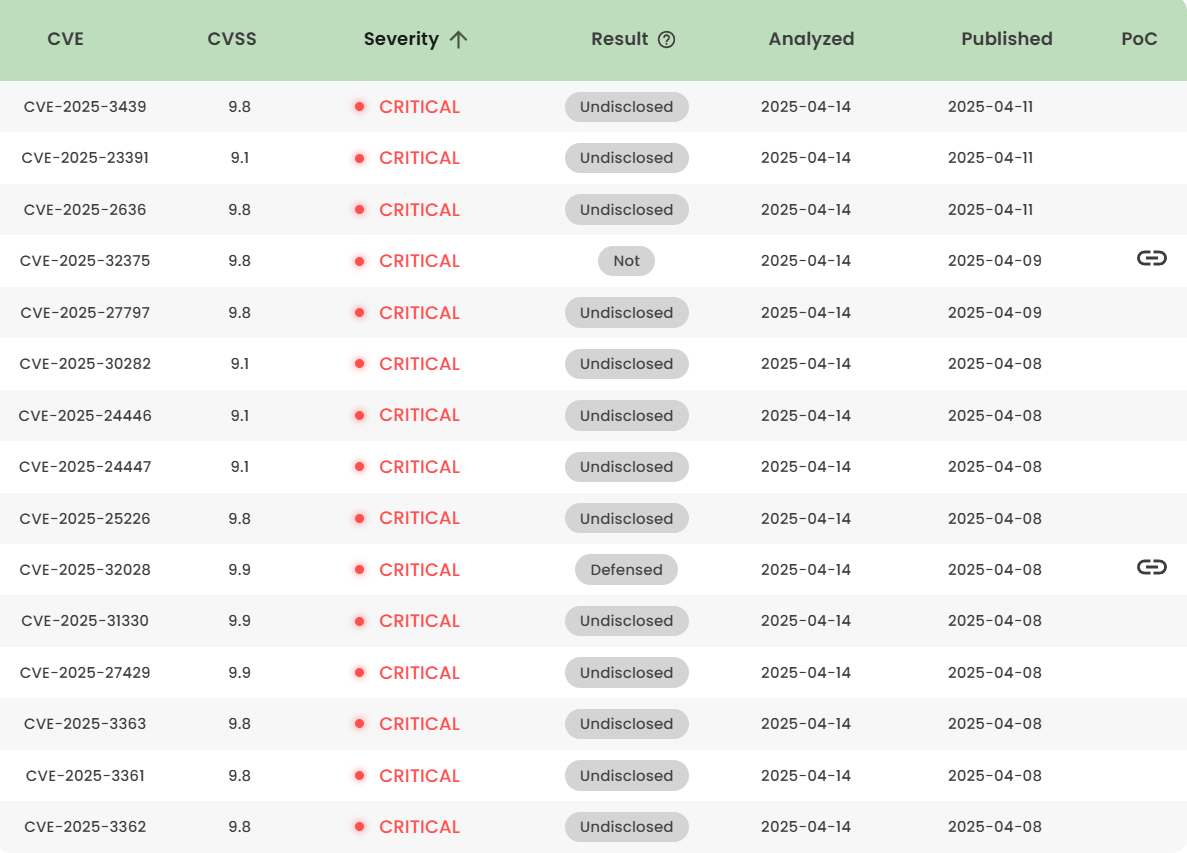
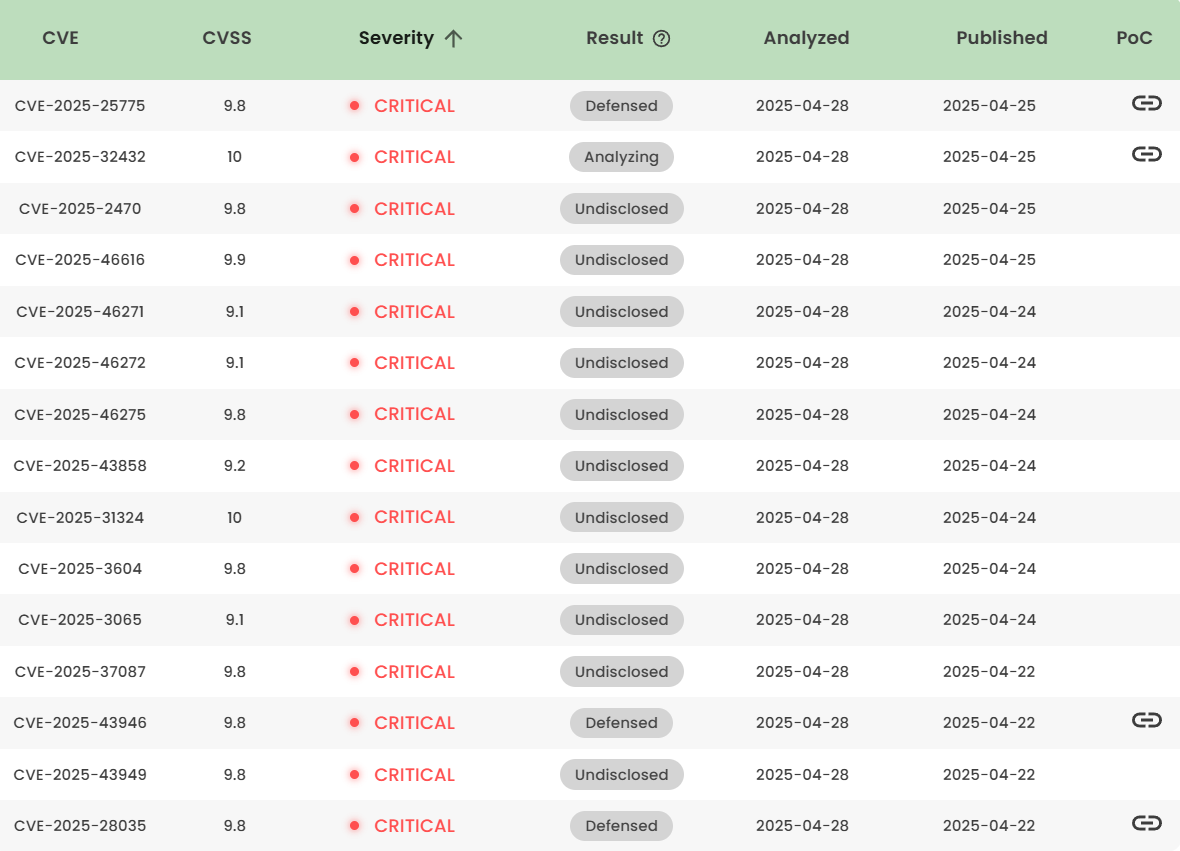
Latest vulnerability CVE status
1. High-risk vulnerability status (2025.04)
2. High-risk vulnerability descriptions