GroupOffice is a system provided to businesses, and the CVE-2025-63406 vulnerability in this service is a critical vulnerability that could allow remote code execution without authentication.
Given the detailed analysis of the vulnerability and the high potential for remote exploitation, exploitation attempts are expected to be active. Therefore, customers using this platform should patch to the latest version as soon as possible.
Our TA team is monitoring vulnerabilities in GroupOffice products and will respond promptly to any related vulnerabilities discovered in the future.
Tags: GroupOffice, RCE, CVE-2025-63406, Remote Code Execution, Intermaesh BV
This report summarizes the technical analysis of CVE-2025-63406, which occurred in a core component of the platform.

Source: https://github.com/Intermesh
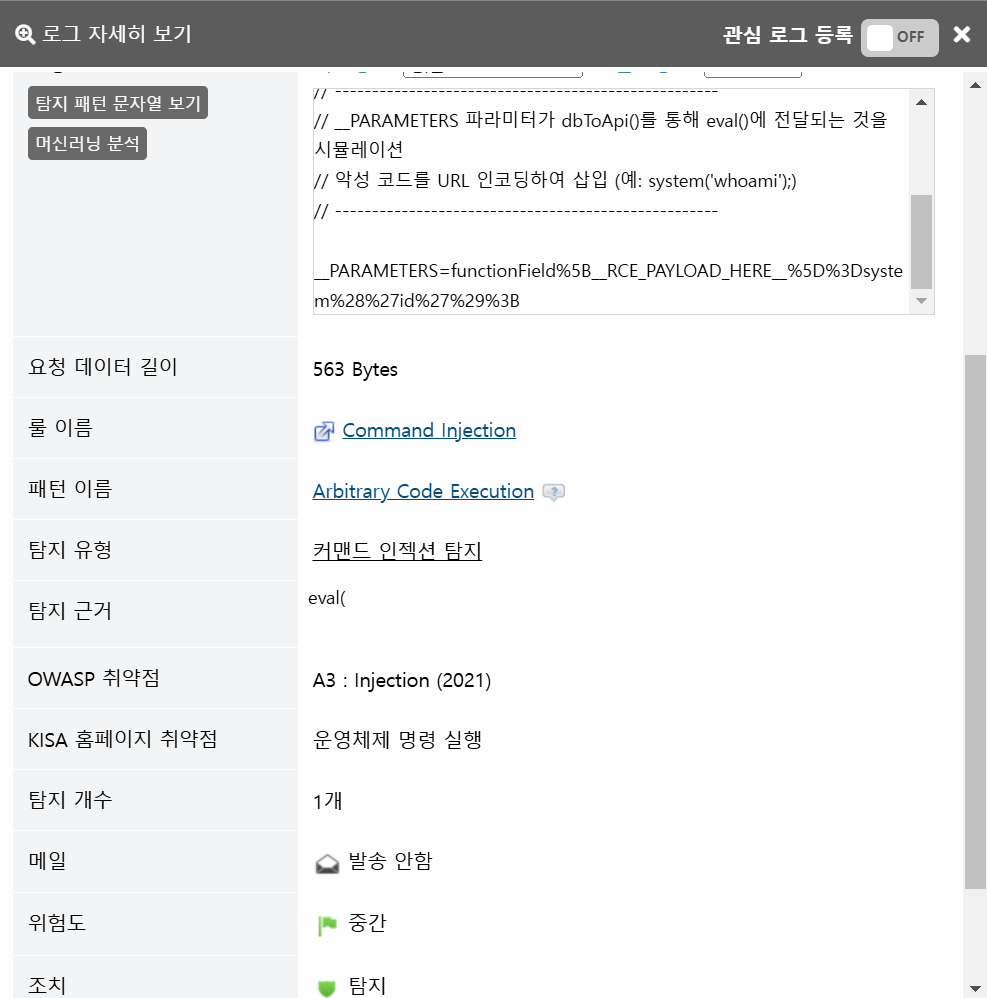
This vulnerability occurs during the processing of the dbToApi() function in the FunctionField.php file. The function fails to properly validate user input, which is combined with PHP’s eval() function in the execution logic.
An attacker can manipulate HTTP request parameters so that the server interprets these inputs as malicious PHP code and executes them. This corresponds to CWE-94 (Code Injection).
Classes and functions used in the attack: The attacker triggers an endpoint that uses FunctionField.php's dbToApi() and eval() functions through a web request to inject a malicious payload.

Source: gemini.google.com
Example attack request:
Immediate update recommendation: Update GroupOffice to v.25.0.47 or later, or v.6.8.136 or later as soon as possible.
Our AIWAF is responding to this vulnerability using the 306: Arbitrary Code Execution detection pattern.
Given the detailed analysis and the high likelihood of remote exploitation, exploitation attempts are expected to be active. Therefore, customers using this platform must apply the latest patch as quickly as possible.
Our TA team continues to monitor vulnerabilities occurring in GroupOffice products and will promptly respond to any related vulnerabilities discovered in the future.
https://nvd.nist.gov/vuln/detail/CVE-2025-63406
https://github.com/WinDyAlphA/CVE-2025-63406-PoC
https://noahheraud.com/posts/CVE-2025-63406/
Given the detailed analysis of the vulnerability and the high potential for remote exploitation, exploitation attempts are expected to be active. Therefore, customers using this platform should patch to the latest version as soon as possible.
Our TA team is monitoring vulnerabilities in GroupOffice products and will respond promptly to any related vulnerabilities discovered in the future.
Tags: GroupOffice, RCE, CVE-2025-63406, Remote Code Execution, Intermaesh BV
1. Overview
GroupOffice is a web-based office management system used to manage content creation, distribution, and collaboration features.This report summarizes the technical analysis of CVE-2025-63406, which occurred in a core component of the platform.

Source: https://github.com/Intermesh
2. Attack Type
CVE-2025-63406 is a Remote Code Execution (RCE) vulnerability that can be exploited over the network without authentication (Pre-Auth RCE).This vulnerability occurs during the processing of the dbToApi() function in the FunctionField.php file. The function fails to properly validate user input, which is combined with PHP’s eval() function in the execution logic.
An attacker can manipulate HTTP request parameters so that the server interprets these inputs as malicious PHP code and executes them. This corresponds to CWE-94 (Code Injection).
Classes and functions used in the attack: The attacker triggers an endpoint that uses FunctionField.php's dbToApi() and eval() functions through a web request to inject a malicious payload.

Source: gemini.google.com
Example attack request:
POST /groupoffice/modules/core/FunctionField.php HTTP/1.1
Host: your-groupoffice-site.com
Content-Type: application/x-www-form-urlencoded
Connection: close
Content-Length: [BODY_LENGTH]
// ---------------------------------------------------- //
__PARAMETERS 파라미터가 dbToApi()를 통해 eval()에 전달되는 것을 시뮬레이션 // 악성 코드를 URL 인코딩하여 삽입 (예: system('whoami');)
// ----------------------------------------------------
PARAMETERS=functionField%5B__RCE_PAYLOAD_HERE%5D%3Dsystem%28%27id%27%29%3B
3. Mitigation
The developer, Intermesh BV, has acknowledged the vulnerability and released a security patch that resolves the issue.Immediate update recommendation: Update GroupOffice to v.25.0.47 or later, or v.6.8.136 or later as soon as possible.
Our AIWAF is responding to this vulnerability using the 306: Arbitrary Code Execution detection pattern.

4. Conclusion
GroupOffice is a system provided for enterprise use, and the CVE-2025-63406 vulnerability found in this service is a critical issue that allows unauthenticated remote code execution.Given the detailed analysis and the high likelihood of remote exploitation, exploitation attempts are expected to be active. Therefore, customers using this platform must apply the latest patch as quickly as possible.
Our TA team continues to monitor vulnerabilities occurring in GroupOffice products and will promptly respond to any related vulnerabilities discovered in the future.
5. References
https://nvd.nist.gov/vuln/detail/CVE-2025-63406
https://github.com/WinDyAlphA/CVE-2025-63406-PoC
https://noahheraud.com/posts/CVE-2025-63406/


