
Before the advent of Zero Trust, traditional network security models implicitly trusted internal users.
Therefore, employees inside the company’s network perimeter and users accessing from outside via VPN, etc. were able to freely access the company’s application. However, this approach was vulnerable to critical threats such as insider collusion, attacks by authorized users, and account takeover, and in particular, exposure to lateral movement was a major concern.
Lateral movement is the process where the attacker moves from one system to another within a network and gains access to resources that are normally inaccessible. Attackers can use social engineering, password cracking, missing patches, or configuration errors to damage internal resources.
Responding to these threats requires a new approach that goes beyond traditional security models.
According to the recent ‘Zero Trust Guidelines 1.0’ of the Ministry of Science and ICT(South Korea), cases of insider collusion or account takeover are increasing. Therefore, this trend exposes loopholes in the implicit trust policies of traditional security.
To counter this, new security strategies such as Zero Trust Architecture (ZTA) are needed.
Zero Trust Architecture (ZTA) continuously verifies all users and devices and enhances data protection.
The core components of ZTA are 'Micro-Segmentation', 'Enhanced Authentication', and 'Software-Defined Perimeter'.
Among these, in this article, we will explain 'Micro-Segmentation'.
Micro-Segmentation
Micro-segmentation is a technology that divides a network into multiple zones or segments.
Micro-segmentation is mainly used in the cloud and virtualized environments and protects sensitive data and systems from cyberattacks by precisely controlling data movement.
On the other hand, Network-segmentation mainly involves separating the network at the physical and logical level and focuses on improving network performance and security.
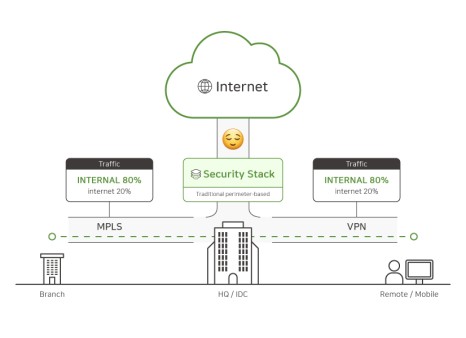
A VPN (Virtual Private Network) is a technology traditionally used to allow remote users to securely connect to a company’s network. However, this technology is essentially similar to allowing users to go anywhere inside a building by simply passing through the main entrance. This may increase security risks by allowing access to the entire network.
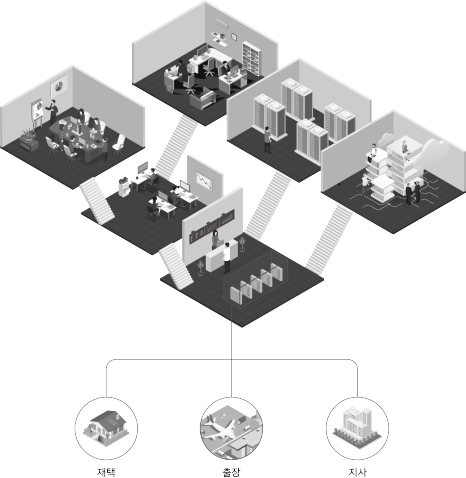
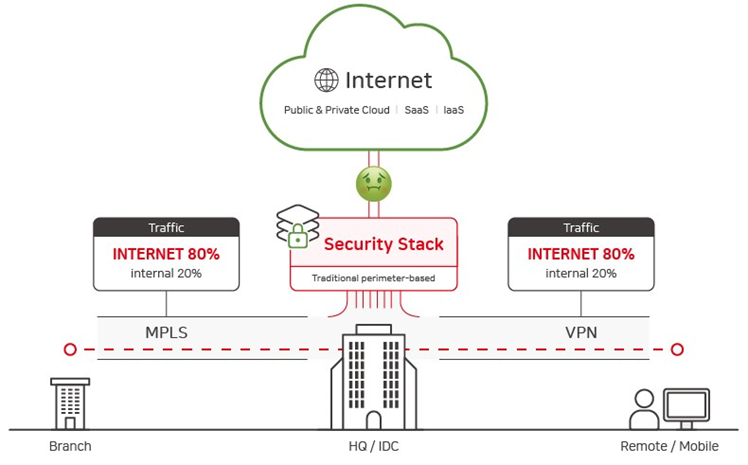
Nonetheless, Zero Trust Network Access (ZTNA) is based on the zero trust principle and overcomes the limitations of VPN by allowing minimal access to only necessary resources. This is similar to hotel guests only being able to access their floor, rooms, and common areas using their room keys. Users can only access certain areas within the building, which enhances security while also improving the user experience.
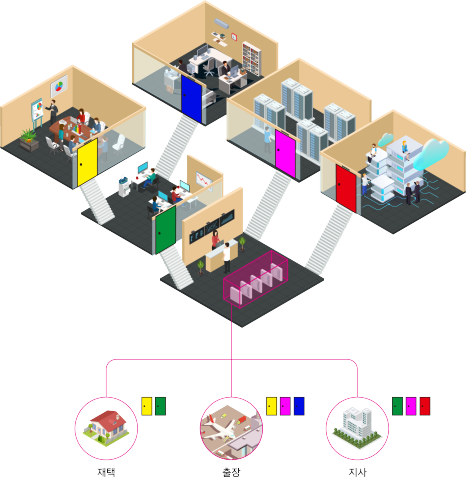
ZTNA solutions, such as AIONCLOUD’s SRA, utilize micro-segmentation to set user-specific access rights to internal applications through conditions such as the user’s country of connection, IP, and device posture.
For instance, if user credentials are stolen or forged by a third party, access can be immediately revoked, effectively blocking threats such as lateral movement.
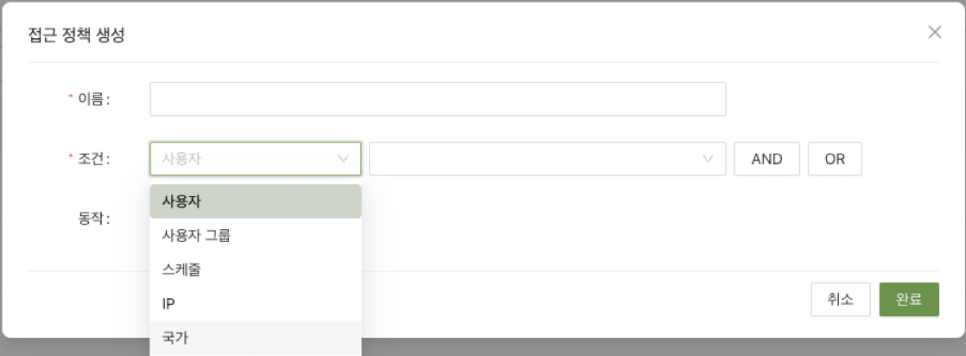
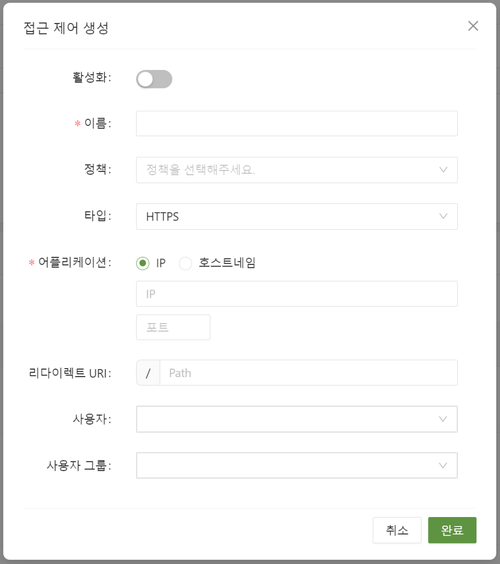
As shown in the image above, you can grant permissions for each application to specific users and user groups.
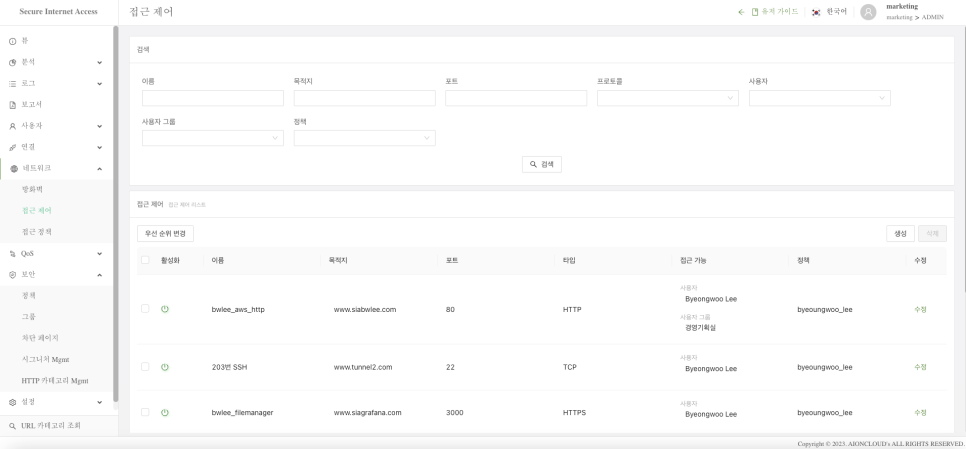
Additionally, after creating a policy, you can manage the permissions of specific users with a few simple clicks.
According to the Zero Trust Principle, all access is denied by default unless otherwise set, and only specific users separately designated through the above procedure are allowed to access specific applications
If you grant the minimum permissions to all users, you can prevent lateral movement and effectively eliminate threats.
In this way, modern security strategies go beyond the limitations of traditional network models to protect internal networks and respond to cybersecurity threats in a more detailed and effective manner.
In an age where technology is constantly evolving, it is essential to select a solution appropriate for the changing security environment.
Keep your company's resources safe and keep pace with the changing times with AIONCLOUD's SRA.
Learn more about [AIONCLOUD Secure Remote Access]


